This is the third installment in our sector spotlight series on the cybersecurity threat landscape in the US Water and Wastewater (WWS), Energy, Communications, and Defense Industrial Base (DIB) critical infrastructure sectors. In this post we:
- provide a Situational Awareness update on the attack surface and potential risks to ICS (Industrial Control System), OT (Operational Technology), and IoT (Internet of Things) devices and networks used in the WWS and other critical infrastructure sectors
- review Iranian, Chinese, and Russian cyber-threat actors targeting U.S. critical infrastructure sectors
- demonstrate two use-cases for a:
- GenAI Analyst Assistant for Shodan
- GenAI Analyst Assistant for Shadowserver
Bottom Line: Despite significant investments in cyber hygiene services, training, and intelligence sharing, many critical infrastructure networks continue to struggle with basic cybersecurity practices. As adversaries grow more sophisticated, failure to improve foundational security measures will leave essential systems vulnerable to disruption, compromise, and exploitation.
Cyber Situational Awareness
On February 27, 2025, the EPA’s Water Infrastructure and Cyber Resilience Division (WICRD), in partnership with WaterISAC, FBI, DHS CISA, and the Office of Intelligence & Analysis (I&A), provided an unclassified threat briefing on cyber and physical threats to U.S. critical infrastructure. The briefing was attended by industry leaders, state and local officials, and federal agencies responsible for securing and defending water and wastewater systems.
While we are unaware of an official release from the briefing, the general understanding is that unless cybersecurity fundamentals and basic cyber hygiene improve, cyber-attacks against the WWS are likely to continue. This assessment is hardly a revelation and has been widely noted by the WaterISAC, EPA, DHS CISA, and cybersecurity researchers [2-17].
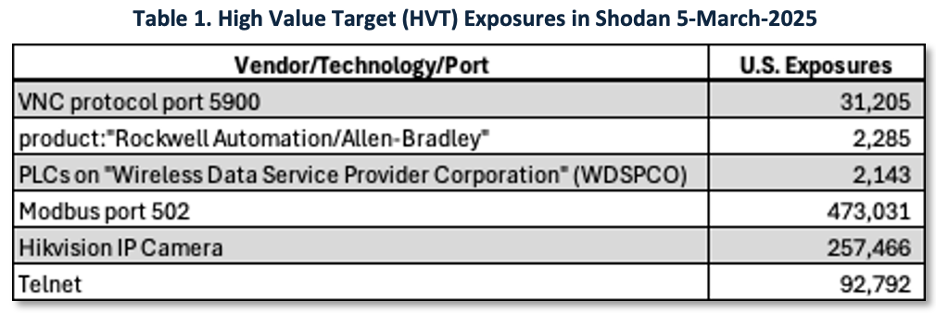
To appreciate the scale of the issues, we made some simple queries in Shodan to find examples of ICS and IoT devices exposed to the public internet in the U.S. In Table 1 we see a selection of high-value targets (HVT) that are publicly accessible, increasing their risk of compromise.
Insights from Shodan Results: The Shodan findings suggest a need for further analysis to better understand:
- Sector Breakdown: Most exposures in the table are in the communications sector. Further analysis is needed on the distribution by organization, industry sector, location, and product versions.
- WWS Attack Surface: A preliminary Shodan estimate of WWS sector exposure reveals nearly 12,000 internet-facing devices across more than 300 organizations, many of which are small, municipally owned utilities. Further analysis is needed to understand WWS devices that are registered to communications and municipal utilities that provide water, electric, and communications.
- Network Segmentation Weaknesses: As noted in our previous research, PLCs (Programmable Logic Controllers) registered to organizations in the communications sector appear to be leaking private IP addresses, indicating poor network segmentation.
- Exploitation Risks: Identified ICS/OT products should be cross-referenced with the CISA Known Exploited Vulnerabilities (KEV) catalog to prioritize patching and mitigation [8].
- Geo-Tagging & Target Analysis: Shodan’s organization, hostname, and geographic filtering can be used to map exposures at the state and city level, aiding in risk prioritization and response planning.
Country Adversary Profiles
Threat actors from Iran, China, and Russia continue to target U.S. Water and Wastewater Systems (WWS) and other critical infrastructure sectors. All three adversaries have incorporated Generative AI (GenAI) into their operations for research, planning, reconnaissance, phishing, and translation. Among them, Iran and China have demonstrated the most extensive use of GenAI technologies [18-20].
Iran – CyberAv3ngers and the Islamic Revolutionary Guard Corps (IRGC): Iranian threat actors, including the IRGC-affiliated CyberAv3ngers and Bauxite, have conducted multiple cyberattacks against U.S. water and wastewater facilities. Targets include facilities in Aliquippa, PA and Vero Beach, FL, which were targeted because of their use of Israeli-made Unitronics PLCs. [7-10]
ODNI (Office of the Director of National Intelligence) attributes 8 attacks in the Water-Wastewater sector in 7 states (Illinois, Ohio, Georgia, South Carolina, Pennsylvania, West Virginia) over a 6-month period (23-Nov-2023 through 22-April-2024) to IRGC or affiliated criminal/hacktivist actors. [11]
China – ‘Typhoon’ groups (Volt, Salt, Flax, Silk): Multiple Chinese cyber actors, including Volt Typhoon (AKA Vanguard Panda) and Salt Typhoon, conduct persistent cyber espionage and pre-positioning operations against U.S. critical infrastructure.
- Volt Typhoon has infiltrated IT networks across multiple U.S. critical infrastructure sectors as a pre-positioning strategy for potential OT disruption, with targets located in the continental U.S. and U.S. territories, including Guam.
- Salt Typhoon, in contrast, has targeted major telecommunications networks, with a primary focus on espionage rather than disruption [12-15].
- CrowdStrike’s 2025 Global Threat Report cites a 150% increase in cyberattacks attributed to Chinese adversaries over the past year.
Russia – Sandworm and Affiliated Hacktivists: Russian state-backed cyber actors, particularly those affiliated with Sandworm (GRU – Military Unit 74455), continue to target U.S. critical infrastructure using proxy hacktivist groups.
- As we previously reported, the People’s Cyber Army (PCA), Z-Pentest, and Cyber Army of Russia Reborn (CARR) have conducted targeted attacks on U.S. water facilities and energy infrastructure. Barracuda researchers attribute CARR’s attacks on water treatment facilities in Muleshoe, Abernathy, Hale Center, and Lockney, TX, as part of a broader campaign against U.S. utilities. The proximity of these attacks to Cannon Air Force Base, home to the 27th Special Operations Wing, suggests a deliberate attempt to target infrastructure supporting military readiness. [16-18]
- ODNI attributes five attacks in the Water-Wastewater sector in 3 states (Texas, Indiana, New Jersey) over a six-month period (23-Nov-2023 through 22-April-2024) to IRGC or Russia-linked a actors.
Assessment: These cyber adversaries demonstrate:
- Strategic Planning – Well-coordinated attacks aligned with national security objectives
- Technical and Operational Innovation – Adaptation to evolving security measures with new tools, like GenAI, and methodologies.
- Stealth and Persistence – Maintenance of long-term access to U.S. networks, often evading detection.
- Plausible Deniability – Nation-state directed operations supported by cybercriminal and hacktivist groups provides plausible deniability.
Each nation-state employs distinct tactics:
- Iran favors direct exploitation of exposed PLCs.
- China specializes in stealthy network infiltration and long-term espionage.
- Russia blends state-sponsored hybrid operations with proxy hacktivist campaigns.
A common U.S. weakness across all attacks is the continued exposure of poorly secured, internet-facing industrial systems. Without immediate improvements in cybersecurity posture, these adversaries will continue to exploit gaps in critical infrastructure defenses.
GenAI Analyst Assistant for Shodan
Specialized search engines like Shodan and Censys are widely used for passive vulnerability assessment, attack surface management, and Internet Intelligence collection. These platforms give cybersecurity teams the ability to identify exposed assets via interactive search, API integration, and dashboards. Shodan provides hundreds of filters and tags for searching by geography, network, organization, product, ports, CVEs, and more.
While Shodan’s interactive tools are powerful, the text-based metadata can be complex and difficult to interpret. Many analysts struggle to understand the significance of metadata fields, assess risks, and determine appropriate mitigation steps.
Use Case: GenAI-Assisted Shodan Analysis: To illustrate the value of a GenAI Analyst Assistant for Shodan, consider the following scenario:
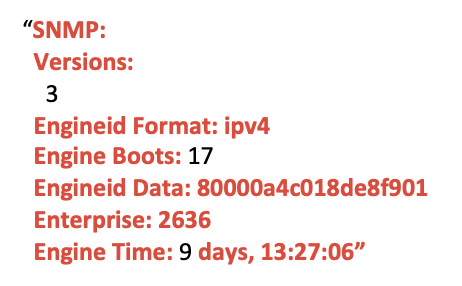
A cybersecurity analyst at a water-wastewater service provider in Florida receives an advisory warning about Simple Network Management Protocol (SNMP) vulnerabilities listed in CISA’s Known Exploited Vulnerabilities (KEV) Catalog – SNMP. [24] Concerned about potential exposure, the analyst searches Shodan and discovers that some of their SNMP servers are publicly accessible. Here’s an example of the Shodan metadata:
The analyst, unfamiliar with SNMP metadata, is unsure about the potential risks or how to mitigate them. Instead of spending hours researching involving others in their task, they use their GenAI Analyst Assistant for help.
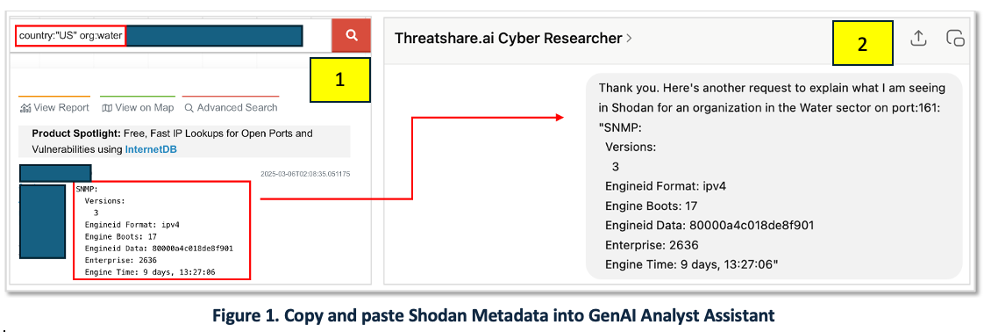
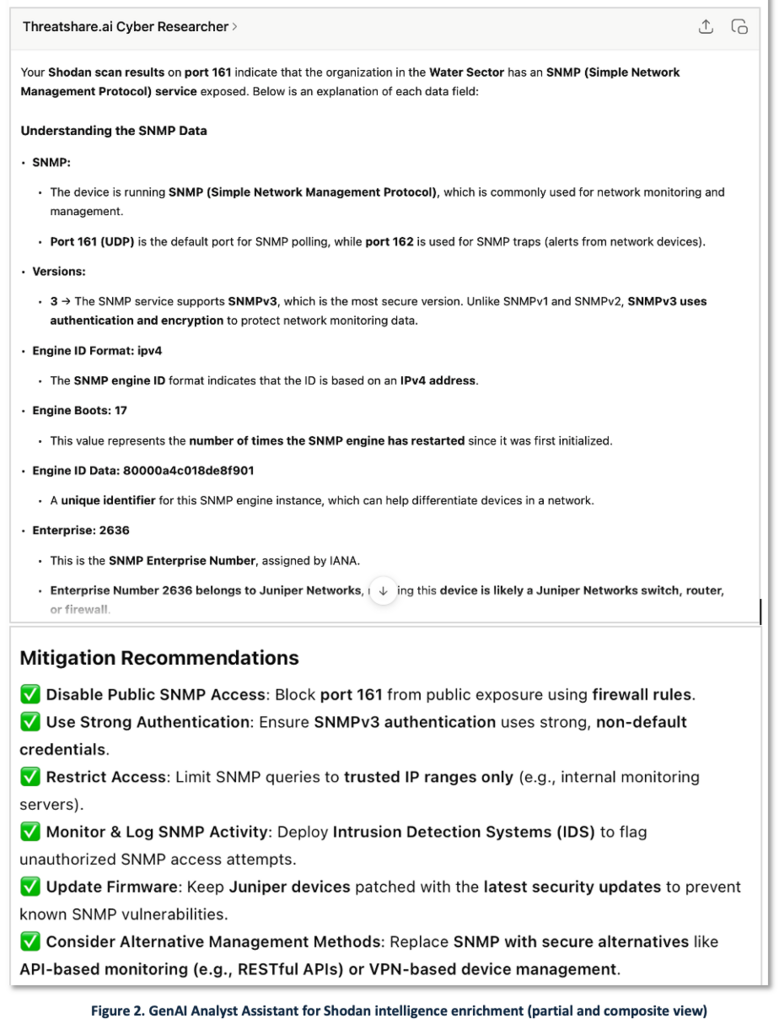
AI-Powered Analysis in Action: Using ThreatShare.ai Cyber Researcher, a customized GPT-based AI assistant, the analyst copies the Shodan metadata (Figure 1, Panel 1) and pastes it into a chatbot prompt (Figure 1, Panel 2).
GenAI’s Response: In Figures 2 and 2b, the AI-generated report is structured into three actionable sections:
- Understanding the SNMP Data – Provides a plain-language explanation of the Shodan metadata. (Figure 2)
- Threat Implications and Risks – Identifies security risks associated with SNMP exposure. (Figure 2.b)
- Mitigation Recommendations – Outlines steps to secure SNMP servers, including patching known vulnerabilities and restricting public access. (Figure 2)
Why this matters: The GenAI Analyst Assistant transforms raw Shodan data into meaningful intelligence, enabling analysts to:
- Quickly interpret complex metadata without advanced protocol knowledge.
- Understand real-world security risks tied to exposed infrastructure.
- Receive clear, actionable mitigation guidance to secure their networks.
As Shodan is a widely used tool in cybersecurity, threat hunting, and third-party risk analysis, this AI-powered approach aids efficiency and decision-making for analysts, researchers, and network security teams.
GenAI Analyst Assistant for Shadowserver
Cybersecurity teams responsible for Operational Technology (OT) and IT network security require timely and actionable intelligence to identify vulnerabilities, track malicious activity, and mitigate cyber threats. This scenario demonstrates how Generative AI (GenAI) can help analysts apply Shadowserver’s network scanning intelligence and time series statistical data in their operations.
Shadowserver’s Role in Cyber Threat Intelligence: The Shadowserver Foundation is a trusted cybersecurity organization dedicated to improving global security by identifying Internet-facing vulnerabilities, tracking malicious activity, and sharing intelligence with governments, CSIRTs (Computer Security Incident Response Teams), law enforcement, and private industry.
Shadowserver operates an internet observatory that collects and analyzes global-scale data using their resources, including:
- Network sensors
- Honeynets and sinkholes
- Botnet monitoring
- Spam and malware tracking
It provides over 100 Report Types covering Internet exposures, vulnerabilities, threat activity, and malware campaigns. These reports are accessible via API and user-configurable dashboards on their public website.
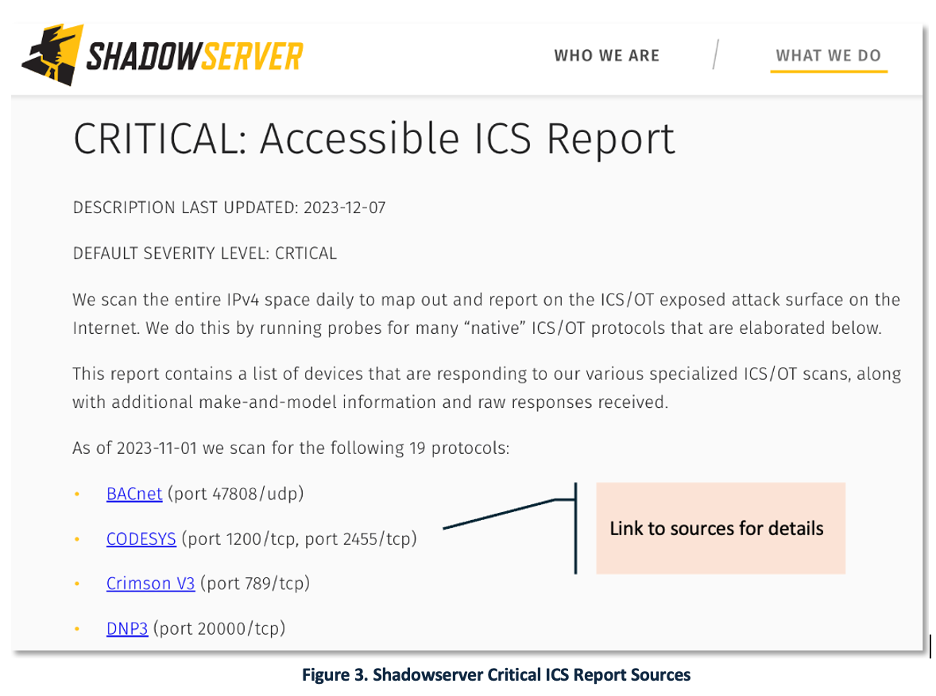
ICS Attack Trends with Shadowserver: A cyber threat analyst is investigating Industrial Control System (ICS) attack trends using Shadowserver’s ‘CRITICAL: Accessible ICS Report’ which provides the exposed attack surface for 19 ICS protocols, as shown in Figure 3. The key intelligence objectives are to:
- Focus on only those six ICS protocols that are relevant to their organization.
- Identify relevant protocols targeted in known attacks by adversaries being tracked.
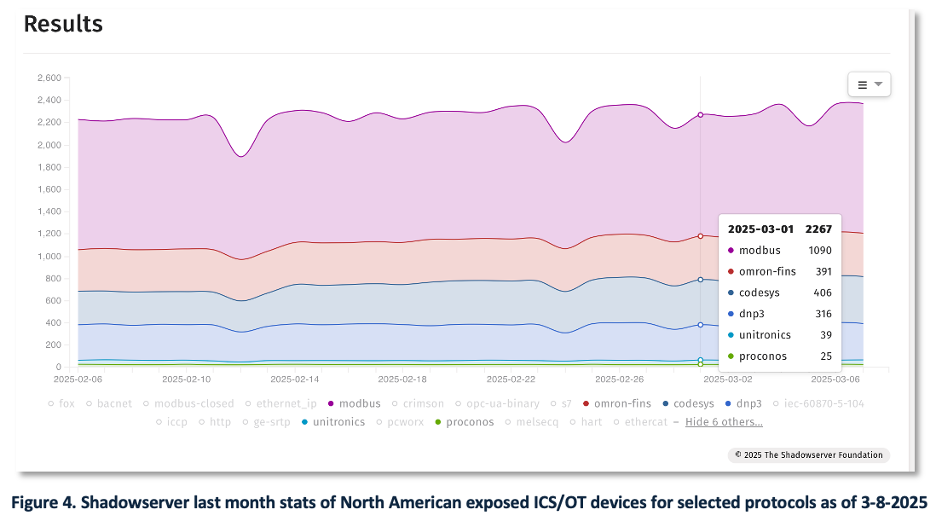
As shown in Figure 4, Shadowserver time series data highlights increases in attack activity for specific ICS protocols. In this example, the analyst notes a spike in Unitronics activity on March 1, signaling a potential emerging threat.
Generating an Adversary Report Using GenAI: A cyber threat analyst working for a Managed Security Services Provider (MSSP), an ISAC, or a government agency is tasked with preparing a threat advisory detailing:
- Relevant ICS protocols & ports, and
- Associated ICS/IoT products using those protocol targeted in cyber-attacks
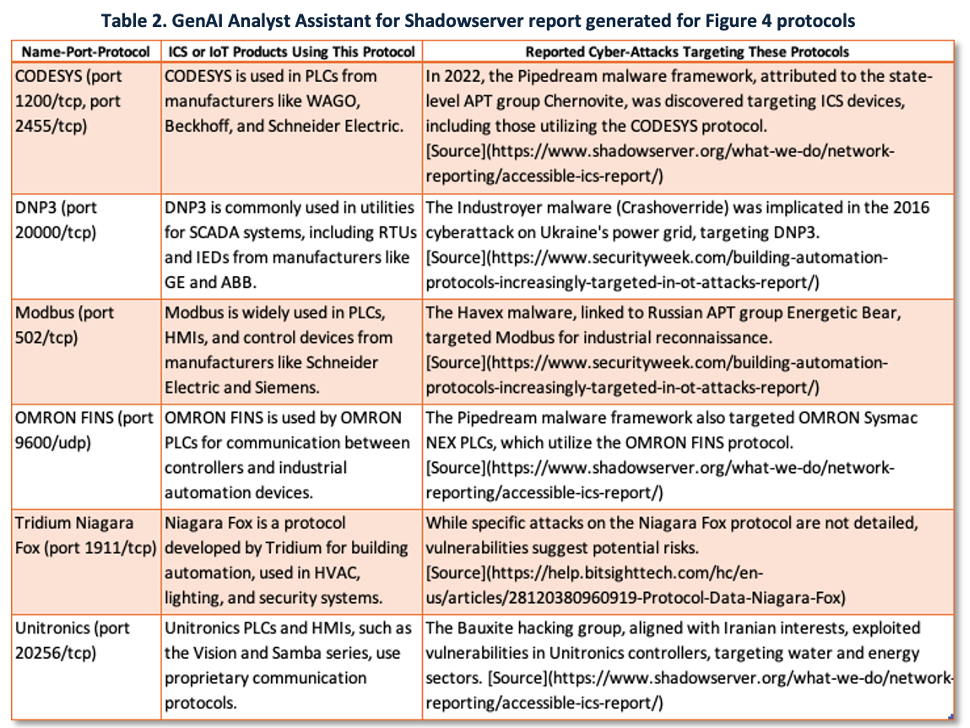
As Shadowserver’s dataset does not directly list ICS products or historical attacks, the analyst uses the GenAI Analyst Assistant to automate report generation using the following prompt:
Using GPT, the AI autogenerated Python code to create the CSV report. The analyst downloaded the CSV, converted it to Excel, and reviewed the preliminary results, as shown in Table 2.
Key Takeaways from this AI-Generated Report:
- While some sources required verification, the overall report was well-structured and provided actionable intelligence.
- The automated process significantly reduced manual research time, demonstrating how GenAI can automate and enhance cybersecurity workflows.
Outlook
If the state-of-the-practice of cybersecurity in critical infrastructure sectors can be characterized as ‘struggling with the fundamentals’, then our adversaries could be characterized as ‘relentlessly innovative, advanced, effective, and undeterred’.
We have previously reported on adversarial use of AI across all stages of cyber operations. [19-20] The FBI, CISA and DC3 (Defense Cybercrime Center) report that threat actors use GenAI for target reconnaissance and use Shodan to identify vulnerable internet-facing devices. [8]
A recent Forbes piece warns adversaries are ‘evolving faster than defenses’ noting that : [30]
- AI-generated phishing emails have a 54% click-through rate compared to 12% for human-written emails’.
- 79% of observed attacks now rely on stolen credentials or identity-based attacks rather than traditional exploits; another reminder that ‘adversaries are logging in rather than breaking in.’
This assessment may be sobering. But it can also be a call to action for defenders to prioritize and accelerate their efforts to protect critical infrastructure sector networks by:
- Strengthening fundamental cybersecurity measures.
- Expanding monitoring beyond network defenses to include accounts, credentials, and Dark Web activity.
- Applying AI-powered cybersecurity to keep pace with adversaries.
Editor’s Notes:
- Acknowledgment to our chatbots for their valuable support in sector classification, research, and editorial review.
- Generated results were subject to a preliminary reasonableness review. Deeper verification is recommended for production use.
References
- EPA – Water and Wastewater Sector Threat Briefing, 27-Feb-2025
- Water-ISAC – 12 Cybersecurity Fundamentals for Water and Wastewater Utilities, December 2024
- Water-ISAC – Cyber Resilience – Cybersecurity Challenges Facing Water Utilities , 2-Jan-2025
- EPA-CISA (TLP:Clear) – Internet-Exposed HMIs Pose Cybersecurity Risks to Water and Wastewater Systems, 13-Dec-2024
- CISA – Guidance and Strategies to Protect Network Edge Devices, 4-Feb-2025
- CISA – EPA Advisory: Internet-Exposed HMIs Pose Cybersecurity Risks to Water and Wastewater Systems, 10-Dec-2024
- CISA: Cybersecurity Advisory, Alert Code AA24-335A – IRGC-Affiliated Cyber Actors Exploit PLCs in Multiple Sectors, Including US Water and Wastewater Systems Facilities, 18-Dec-2024
- CISA (FBI-DC3) Alert CodeAA24-241A – Iran-based Cyber Actors Enabling Ransomware Attacks on US Organizations, 28-Aug-2024
- Dragos – Threat Group / Bauxite
- Dragos – Dragos Reports OT/ICS Cyber Threats Escalate Amid Geopolitical Conflicts and Increasing Ransomware Attacks, 25-Feb-2025
- ODNI: CTTIC – Recent Cyber Attacks on US Infrastructure Underscore Vulnerability of Critical US Systems, November 2023–April 2024, June 2024
- CISA Blog – Strengthening America’s Resilience Against the PRC Cyber Threats, 15-Jan-2025
- Warontherocks.com – A Tale of Two Typhoons: Properly Diagnosing Chinese Cyber Threats , 25-Feb-2025
- Industrial Cyber – DHS warns Chinese-made internet cameras pose espionage threat to US critical infrastructure, 10-Feb-2025
- Cybersecurity Dive – CISA, FBI confirm critical infrastructure intrusions by China-linked hackers, 7-Feb-2024
- CISA – Joint Advisory: Defending OT Operations Against Ongoing Pro-Russia Hacktivist Activity, 1-May-2024
- Barracuda Networks – Infrastructure defense: Water and wastewater systems, 26-Dec-2024
- Trellix – Blurring the Lines: How Nation-States and Organized Cybercriminals Are Becoming Alike, 14-Jan-2025
- Google Threat Intelligence Group (GTIG) – Cybercrime: A Multifaceted National Security Threat, 11-Feb-2025
- Google Threat Intelligence Group (GTIG) – Adversarial Misuse of Generative AI, 29-Jan-2025
- Wisdiam – 11 recent cyber-attacks on the water and wastewater sector, 13-Oct-2024
- Axios Codebook – 1 big thing: State-linked hackers share their most dangerous tools, 25-Feb-2025
- CISA Enhanced Visibility and Hardening Guidance for Communications Infrastructure , 4-Dec-2024
- CISA (KEV Catalog) – Known Exploited Vulnerabilities Catalog – SNMP
- Claroty:Nexus – Identifying, Classifying Riskiest Devices in OT-Heavy Environments, 25-Feb-2025
- ReliaQuest Threat Landscape Report: Uncovering Critical Cyber Threats to Utilities , 10-Dec-2024
- Ivanti – Security Advisory Ivanti Connect Secure, Policy Secure & ZTA Gateways (CVE-2025-0282, CVE-2025-0283), Created 8-Jan-2025, Update 21-Jan-2025
- NIST – NIST Special Publication NIST SP 800-82r3 Guide to Operational Technology (OT) Security, Sept 2023
- IC3.gov: CISA, FBI, EPA – Incident Response Guide Water and Wastewater Sector, January 2024
- Forbes – Cyber Threats Are Evolving Faster Than Defenses, 6-March-2025