In recent years the CISO job has evolved from technical advisor to strategic advisor for C-Suite executives. As GenAI and Cybersecurity topics have become mainstream and business news, CISOs and their teams must be prepared to answer C-suite questions on a regular basis along the lines of:
- ‘Hey, have you heard about this?
- How does it affect us?
- What are we doing about it?
In this post, we look at three high profile topics from the past few weeks:
- Adversary Intelligence: What should we know about the Chinese “Typhoon” threat actors?
- Vulnerability Intelligence: How do we respond to the CitrixBleed 2 vulnerability?
- GenAI Readiness: What lessons from early GenAI projects apply to our cybersecurity teams?
Big Picture: Cyber threats move at machine speed. Today’s urgent alert will be replaced by others tomorrow. AI hype induces AI and cyberthreat fatigue. Many GenAI pilots stall before delivering value.
Lessons learned from successful projects are instructive. Successful companies foster a culture of experimentation, encourage training, build team confidence with early wins, and focus on augmenting rather than eliminating staff. Successful projects assure that data collections meet general standards of data quality (relevance, timeliness, accuracy, completeness) and governance. As CISOs plan their strategies and operations, it’s important to not overthink, iterate and keep moving forward, and stay one step ahead of adversaries.
Adversary Intelligence
What Is Cyber Threat Intelligence (CTI)?
CTI, a superset of Adversary Intelligence, is the discipline of gathering, enriching, and analyzing data on cyber threats—malware signatures, IPs, domains, TTPs, and more—to guide defensive actions. CTI is available from thousands of proprietary and open sources (OSINT) in both structured (machine readable) and unstructured formats. It is used for tactical, technical, operational, and strategic analysis.
What Is Adversary Intelligence?
A subset of CTI, Adversary Intelligence focuses on profiling the people behind attacks. It explains the:
- Who: Actor identities, front companies, hack-for-hire networks
- Why: Motivations and objectives (espionage, disruption, profit)
- How: Preferred tools, infrastructure, and campaign histories
What Is Adversary Attribution?
Actor attribution is the process of identifying and linking cyberattacks to the specific individuals, groups, or nation-states responsible by analyzing technical evidence (TTPs, infrastructure) and contextual intelligence (motives, capabilities). Actor attribution is more art than science. Key challenges include:
- Naming Divergence: CrowdStrike tracks 250+ actors; Microsoft tracks 1,600. MITRE ATT&CK lists 170 groups with 390 aliases.
- Alias Overlap: The same actor may be “Salt Typhoon” (Microsoft) and “Operator Panda” (CrowdStrike), or up to 48 different names in U.S. government reports.
- Standardization Efforts: Industry collaborations like the CTI Sharing Initiative aim to harmonize taxonomies, but competitive pressures can impede information sharing. [25-28]
With this foundation, we can now examine how the Typhoon family—Salt, Volt, Silk, and Flax—uses front companies, hacktivists, cybercriminals, and commercial internet infrastructure providers to evade attribution and sustain long-term espionage campaigns.
Typhoon Adversary Groups
Defining the Typhoon Family
The Typhoon family comprises four Chinese state-sponsored APT groups—Volt, Salt, Silk, and Flax Typhoon—each executing cyber-espionage and pre-positioning operations against critical infrastructure, government, and private targets globally.
Navigating the OSINT Hype
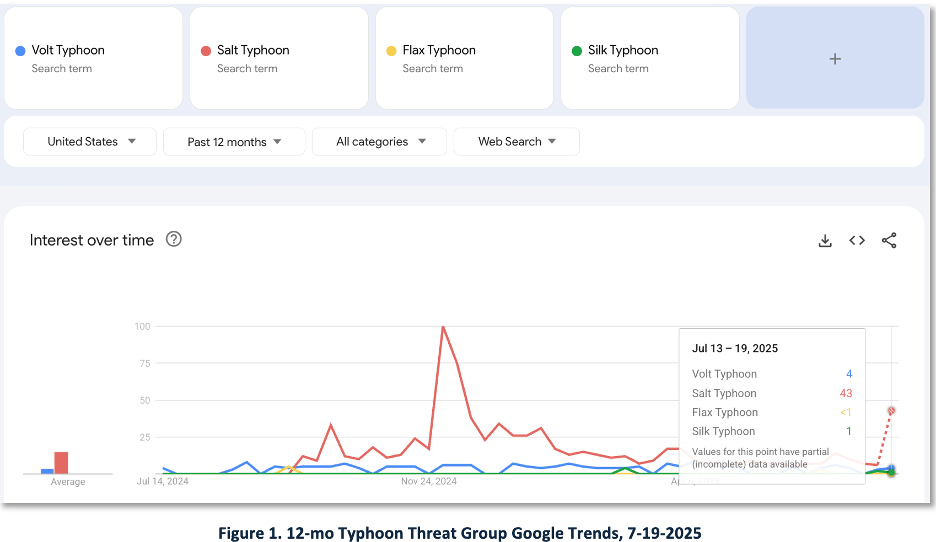
With dozens of blog posts and media articles—often amplified by AI—security teams struggle with information overload. Our 18 authoritative sources [1-18] from Q1–Q3 2025 and our Google Trends dashboard (Figure 1) confirm that Salt Typhoon dominates the conversation.
GenAI-Powered Research Workflow
To cut through the noise, we’ve customized our ThreatShare.ai ChatGPT instance to:
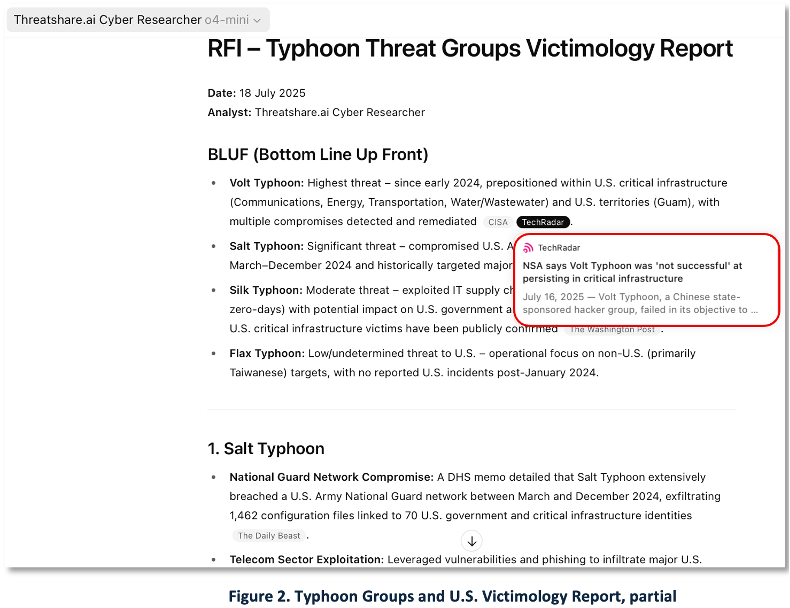
- Track Multiple Actors (Figure 2): We prompt ChatGPT to list recent incidents per Typhoon group, then verify accuracy by inspecting source links.
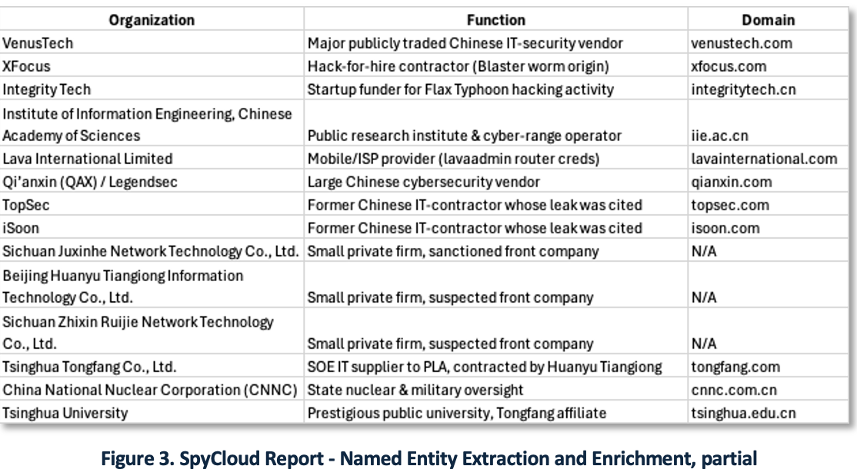
- Extract & Enrich Entities (Figure 3): Using ChatGPT’s NLP NER capabilities, we automatically identify organizations, roles, and domain names—augmenting sparse reports with live WHOIS and company-info lookups. The SpyCloud report provided valuable intelligence derived from Dark Web forums and data leak sites (DLS). In Figure 3, we see an example of how we used ChatGPT’s Named Entity Extraction (NER) capability to extract and summarize the many entities and their roles mentioned in the report. And in column 3, we show how we used to ChatGPT to enrich the source report with information that was not contained in the source by looking up the domain names for the extracted entities.
This hybrid human–AI approach ensures we report the most relevant Typhoon-family insights while maintaining rapid, source-centric validation, an important capability for threat-hunting and executive briefings.
Global Blended Operations
Attribution becomes especially challenging when nation-state actors collaborate with cybercriminals, hacktivists, and commercial service providers—a pattern seen not only in China but also in Russia, Iran, North Korea, and Ukraine. Insights from the SpyCloud Dark Web profile on Salt Typhoon prompted us to map out these complex relationships using GenAI and OSINT sources [1.2].
China’s Red Hacker Ecosystem
A July 2025 Research Report from the Center for Security Studies (CSS), ETH Zürich details how China’s PLA and MSS orchestrate “Red Hacker Groups” by blending [19,20]:
- Criminal Networks & Hack-for-Hire: Underground forums and patriotic hacker collectives
- Commercial IT Vendors: Major firms like Baidu, Alibaba, and Huawei
- Security & Infrastructure Providers: Companies such as Venustech, Topsec, and NSFocus
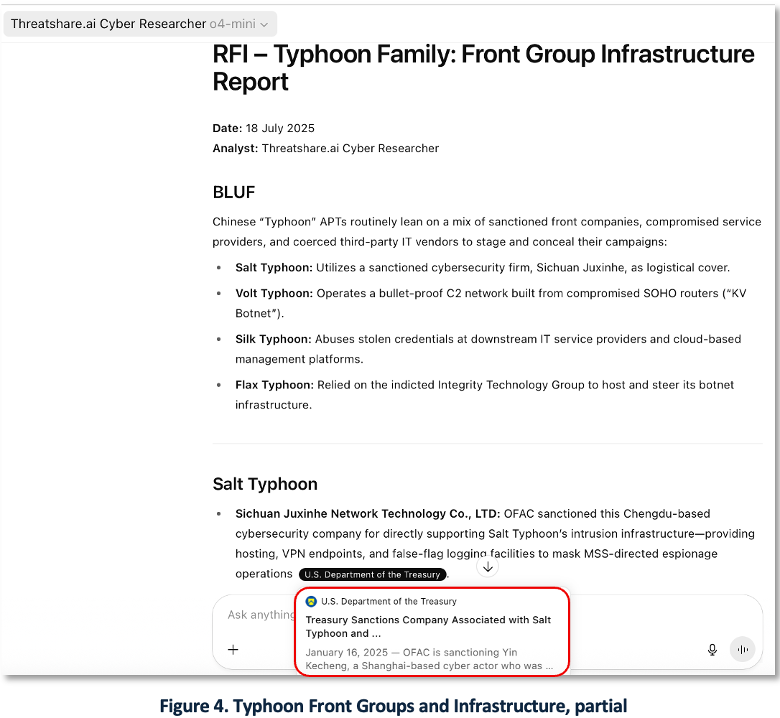
Figure 4 shows how these front-company relationships support the Typhoon family’s infrastructure. By feeding this ecosystem map into our ThreatShare.ai ChatGPT instance, we can query connections—e.g., which front firms supply VPN endpoints to Salt Typhoon—and validate results against authoritative sanctions lists and corporate registries. This GenAI-assisted approach can transform unstructured OSINT into structured data, enabling analysts to trace how front groups enable Typhoon operations and strengthen collective defense.
Vulnerability Intelligence
Salt Typhoon Breach of U.S. National Guard Networks
In June 2025, the DHS Office of Intelligence and Analysis (OIA) detailed a Salt Typhoon intrusion into a U.S. National Guard network spanning March–December 2024. The first public mention on OIA report was on 15-July-2025 [16,17,24,33]. The adversary exfiltrated:
- Network configuration files and diagrams
- Traffic logs across 50 states and four U.S. territories
- Administrator credentials enabling follow-on attacks
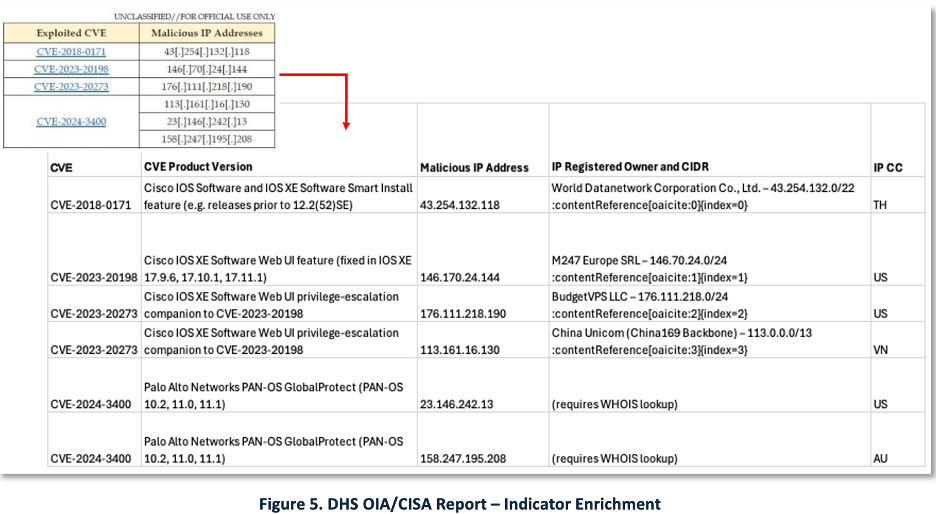
The OIA report included a two-column table of exploited CVEs and malicious IPs (top-left, Figure 5). On 24 Jun 2025, SOCRadar confirmed Salt Typhoon’s exploitation of CVE-2023-20198 and CVE-2023-20273 in Cisco devices—and warned of NetScaler vulnerabilities [24].
Using GenAI, we transformed and enriched the raw OIA table (bottom of Figure 5). Our GPT scripts:
- Fetched CVE product details for each entry
- Parsed text-based IP lists into structured rows
- Added WHOIS-derived owner and country codes
While the results need to be refined, this rapid enrichment demonstrates how analysts can generate verified, structured vulnerability intelligence without requiring developer support.
CitrixBleed 2
CISA Emergency Directive: On 10-July-2025, CISA added the “Citrix Bleed 2” bug, tracked as CVE-2025-5777, to its Known Exploited Vulnerabilities (KEV) list and issued a directive to federal agencies to patch within 24 hours [23], far faster than the typical 5–23 day window and a reflection of the critical severity risk [15, 21,22, 23, 34].
Early Exploitation: GreyNoise observed active exploitation beginning 23 June 2025—two weeks before any public proof-of-concept—and published a blocklist of malicious IPs used in scans.
Broad Impact: On July 18, SecurityWeek reported:
- ≥ 100 organizations across education, finance, government, legal, tech, and telecom have been targeted.
- At least 26 attacker IPs (from China, Russia, South Korea, and the U.S.) conducted exploitation attempts.
- The Shadowserver Foundation data shows ~4,700 NetScaler instances remain unpatched as of 17 July 2025.
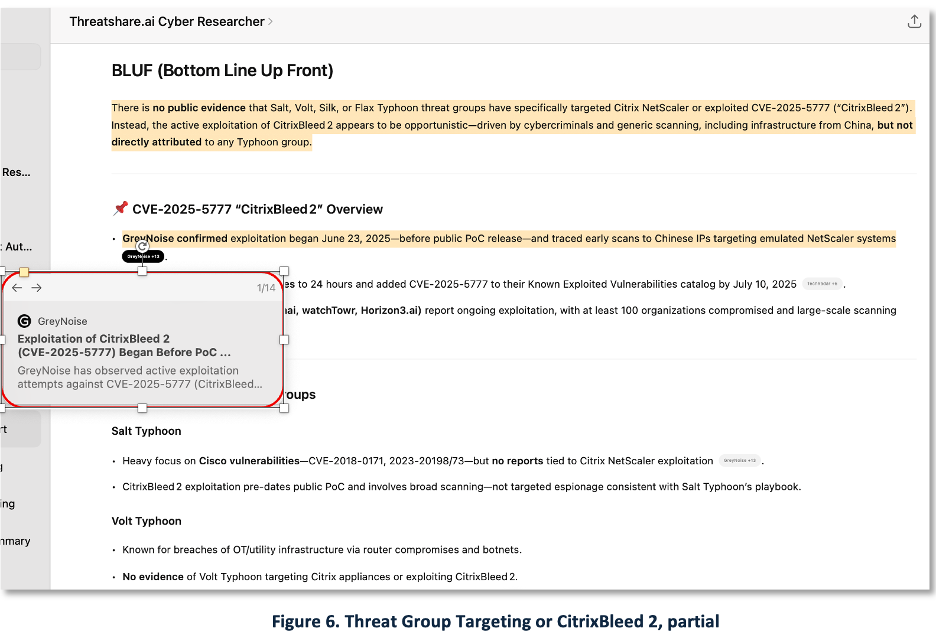
Typhoon Linkage Check: On 19 July 2025, we queried our ThreatShare.ai ChatGPT for any Typhoon-family involvement. As shown in Figure 6, GPT found no evidence tying Salt, Volt, Silk, or Flax Typhoon to CitrixBleed 2 exploitation—consistent with the broad, opportunistic scanning patterns observed, rather than targeted espionage.
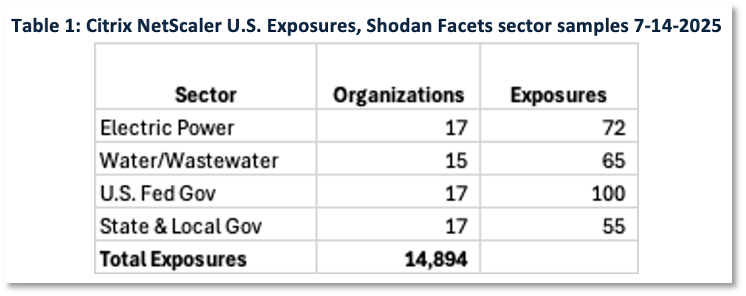
Building on DoublePulsar’s published Shodan query for Citrix NetScaler and Gateway devices, we ran an updated search scoped to U.S. IP ranges. We then applied Shodan’s “Facets” feature to group results by organizational sector—Electric Power, Water/Wastewater, Federal Government, and State & Local Government—and manually sampled the top organizations in each category. Table 1 summarizes the total NetScaler exposures found in this feasibility demonstration. These manually compiled figures represent a small sector-sample only, intended to illustrate how targeted sector-level intelligence can highlight relative risk exposures.
Big Picture
CISOs in critical-infrastructure organizations juggle three hats: technical expert, organizational leader, and strategic advisor to the C-Suite. They must understand complex IT/OT architectures, ensure team training and upskilling (where GenAI can accelerate learning), and translate cyber risk into business terms for senior executives.
To illustrate how GenAI supports this complex role, consider the three executive questions we opened with, and evaluate the sample ChatGPT-generated responses tailored for a large electric-power utility:
- “Have you heard about this?”
“This refers to Salt Typhoon, a Chinese state-sponsored APT targeting telecoms and energy, and CitrixBleed 2(CVE-2025-5777), a critical NetScaler memory-leak vulnerability on CISA’s KEV list as of 10 July 2025.” - “How does it affect us?”
“Salt Typhoon’s playbook includes long-term pre-positioning in power-grid OT networks, enabling reconnaissance and disruption. CitrixBleed 2 exposes our NetScaler management interfaces—over 4,700 unpatched instances pose a severe operational risk.” - “What are we doing about it?”
“We’ve segmented our OT/IT zones and deployed IDS rules tuned to Typhoon TTPs. For CVE-2025-5777, emergency patches were applied within CISA’s 24-hour window, and remediation is validated against Shadowserver scan data.”
So, what do we think about these answers? If we did our executive reading, we might recall that GenAI are in essence, ‘plausibility engines’ that give answers that may seem coherent, persuasive, and even intelligent [30,31,32,29]. However, outputs are only as reliable as the data and prompts provided. When absolute accuracy is critical, human verification of all AI-generated recommendations is essential.
Editor’s Notes:
- Thanks to our GenAI assistants: ChatGPT-4o, ThreatShare.ai Cyber Researcher, Google Gemini AI, Anthropic Claude, and Perplexity. We used these to assist with search, brainstorming, summarization, entity extraction, transformation and enrichment, script and code generation, and editorial review.
- The featured image is an edited composite from Cyber Security News, ChatGPT, Cybercrank, and Wired / Staff Getty Images
References
- SpyCloud Labs – State Secrets for Sale: More Leaks from the Chinese Hack-for-Hire Industry, 1-July-2025.
- Natto Team | Natto Thoughts – Salt Typhoon: the Other Shoe Has Dropped, but Consternation Continues, 22-Jan-2025.
- SOCRadar – Dark Web Profile: Salt Typhoon, 15-Feb-2025
- Cisco Talos – Weathering the storm: In the midst of a Typhoon, 20-Feb-2025.
- Tenable – Salt Typhoon: An Analysis of Vulnerabilities Exploited by this State-Sponsored Actor, 23-Jan-2025.
- RecordedFuture: Insikt Group – RedMike (Salt Typhoon) Exploits Vulnerable Cisco Devices of Global Telecommunications Providers, 13-Feb-2025. https://go.recordedfuture.com/hubfs/reports/cta-cn-2025-0213.pdf
- Varonis – Salt Typhoon: The Threat Group Behind Major Cyberattacks, 5-March-2025.
- Hack the Box – Inside Salt Typhoon: How Chinese APTs breached US telecoms (and stayed hidden for years), 9-July-2025.
- CISA Cybersecurity Advisory, Alert CodeAA24-038A – PRC State-Sponsored Actors Compromise and Maintain Persistent Access to U.S. Critical Infrastructure , 7-Feb-2025.
- U.S. Department of Justice – Justice Department Announces Arrest of Prolific Chinese State-Sponsored Contract Hacker, 8-July-2025
- U.S. Department of the Treasury – Treasury Sanctions Company Associated with Salt Typhoon and Hacker Associated with Treasury Compromise, 17-June-2025. https://home.treasury.gov/news/press-releases/jy2792
- Microsoft – Silk Typhoon targeting IT supply chain, 5-March-2025
- CyberScoop – Top FBI cyber official: Salt Typhoon ‘largely contained’ in telecom networks, 2-July-2025.
- Just Security – What It Takes to Stop the Next Salt Typhoon, 15-July-2025.
- SecurityWeek – CitrixBleed 2: 100 Organizations Hacked, Thousands of Instances Still Vulnerable, 18-July-2025.
- Wired – Security News This Week: China’s Salt Typhoon Hackers Breached the US National Guard for Nearly a Year, 19-July-2025.
- NextGov/FCW – Salt Typhoon hacks into National Guard systems a ‘serious escalation’, experts warn, 16-July-2025.
- The Record |Recorded Future News – NSA: Volt Typhoon was ‘not successful’ at persisting in critical infrastructure, 15-July-2025.
- Wired – How China’s Patriotic ‘Honkers’ Became the Nation’s Elite Cyberspies, 18-July-2025.
- Report – Center for Security Studies (CSS), ETH Zürich, Before Vegas: The “Red Hackers” Who Shaped China’s Cyber Ecosystem, July 2025.
- GreyNoise – Exploitation of CitrixBleed 2 (CVE-2025-5777) Began Before PoC Was Public, 16-July-2025.
- DoublePulsar – CitrixBleed 2: Electric Boogaloo — CVE-2025–5777, 24-June-2025.
- The Record |Recorded Future News – CISA orders agencies to immediately patch Citrix Bleed 2, saying bug poses ‘unacceptable risk’, 11-July-2025.
- SOCRadar – Chinese APT Exploits Cisco IOS XE Vulnerabilities (CVE-2023-20198 & CVE-2023-20273) in Global Attacks, update 24-June-2025.
- MITRE ATT&CK Group. https://attack.mitre.org/groups/
- CrowdStrike – https://www.crowdstrike.com/en-us/platform/ai/, 12-July-2025
- Microsoft – Microsoft Digital Defense Report 2024
- Reuters – ‘Forest Blizzard’ vs ‘Fancy Bear’ – cyber companies hope to untangle weird hacker nicknames, 2-June-2025
- DataBreachToday – Why ‘AI Fatigue’ Is Risky to Cyber Leaders and Their Teams, 15-July-2025.
- NYTimes – Musk’s Chatbot Started Spouting Nazi Propaganda. That’s Not the Scariest Part., 11-July-2025.
- Forbes – AI Without Data Discipline Is Just Hype, Says JPMorganChase’s CPO For Data And AI, 18-July-2025.
- Brilliance Security Magazine – How Data Quality Impacts your Cybersecurity Posture., 20-Feb-2024
- DHS Office of Intelligence and Analysis (OIA) – DHS-IA-IF-2025-08873 | (U//FOUO) Salt Typhoon: Data Theft Likely Signals Expanded Targeting, 11-June-2025
- Imperva – CVE-2025-5777 Exposes Citrix NetScaler to Dangerous Memory Leak Attacks, 11-July-2025