Feedback on last week’s post about Salt Typhoon’s CitrixBleed 2 campaign has been overwhelmingly positive, both in terms of the technical analysis and our “three executive questions for CISOs” framework. With Typhoon-related threats still dominating headlines, this blog serves as a sequel that examines the latest attacks.
This week, the spotlight is on ToolShell; an unauthenticated RCE (Remote Code Execution) in on-premises Microsoft SharePoint (CVE-2025-53770). Unlike the NetScaler-focused CitrixBleed 2 exploits, the ToolShell exploit chain is used by multiple Chinese “Typhoon” groups to compromise SharePoint servers for espionage and, in the case of Storm-2603, ransomware deployment.
Maintaining our executive Q&A format, we’ll address three senior executive questions that every CISO should be ready to answer:
- “Have you heard about this?”
– Understanding the basics of the ToolShell RCE campaign. - “How does it affect us?”
– Assessing the risk to large enterprises in sectors like business services, finance, and government. - “What are we doing about it?”
– Outlining both immediate mitigations for SharePoint RCE and broader defenses against RCE-based attacks.
Impact Assessment: We evaluate this campaign from two angles:
- Narrow view: RCE attacks against on-prem SharePoint (CVE-2025-53770) by a focused set of Chinese threat actors.
- Broad view: A spectrum of Chinese APTs exploiting RCE flaws across multiple network products and CVEs.
In every scenario, these adversaries demonstrate high sophistication, targeting critical infrastructure and national-security assets. We’ll illustrate how CISO teams can leverage OSINT CTI and generative AI to anticipate, detect, and defend against both targeted and widespread RCE threats.
ToolShell SharePoint RCE Summary
Sources and Collections
Sources for this project were collected from open source (OSINT) blogs published by authoritative CTI providers [1-11], journalists and news organizations [12-19]. Many of CTI sources are members of the Cyber Threat Alliance, a collective intelligence organization that shares vetted threat intelligence.
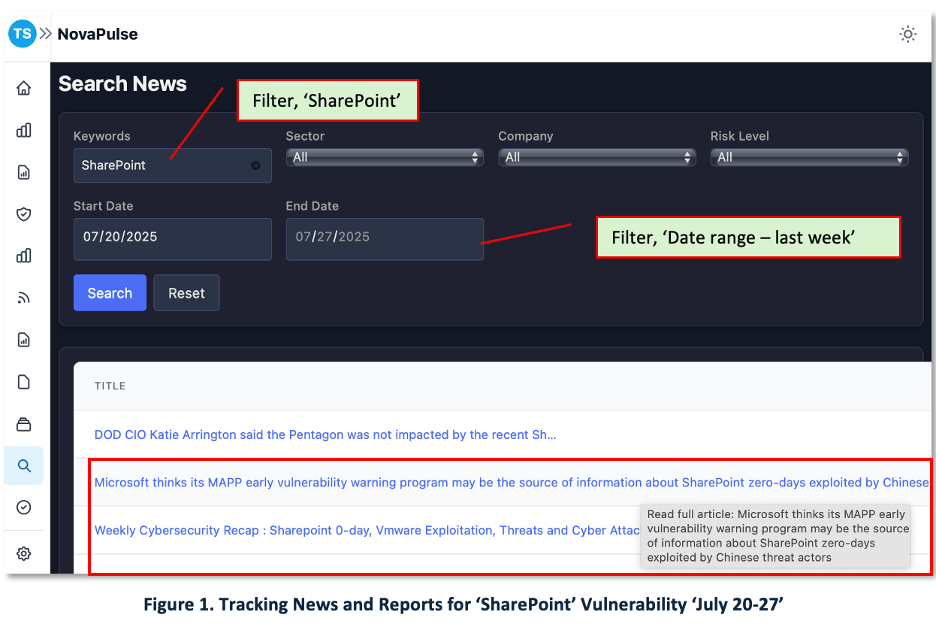
To accelerate our research, we are piloting NovaPulse, our machine-learning CTI aggregator that clusters individual threat-intel articles into actionable, incident-level alerts. Between July 20–27, NovaPulse ingested over 700 SharePoint-related reports and programmatically surfaced high-precision alerts. Figure 1 provides a snapshot of the NovaPulse dashboard, showing how results can be filtered and grouped by sector, company, and risk level.
Campaign Summary
The ToolShell RCE campaign represented a direct exploitation of several zero-day flaws in on-premises SharePoint; namely CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE-2025-53771. All three threat actors – Chinese nation-state groups Linen Typhoon and Violet Typhoon, and the cybercriminal group Storm-2603 – exploited the same vulnerabilities. CVE-2025-53770 is rated “critical” (9.8/10), with all initial access achieved via remote code execution.
Once inside, Linen Typhoon and Violet Typhoon deployed web shells that they could use to steal sensitive data, whereas Storm-2603 weaponized the RCE to harvest high-value enterprise information from SharePoint and then deploy ransomware for financial gain. According to Microsoft, Storm-2603 began its ransomware campaign on July 18, 2025 [3].
As of July 23 there have been reports of approximately 400 compromised systems [1,12,13]. Check Point reports that 35 percent of the attacks occurred in the United States (none in China), with the top targets being Business Services (22 percent), Financial Services (19 percent), and Government (14 percent). The victims list includes high-profile U.S. Government organizations such as the US National Nuclear Security Administration, Department of Energy, DHS, NIH, and Department of Education. We have not seen numbers on the number of ransomware attacks.
SANS advises that any organization running vulnerable, internet-facing SharePoint servers should assume compromise and implement remediations and mitigations – patching alone is no longer sufficient. More threat groups are expected to exploit the still-vulnerable SharePoint systems in the coming weeks. [13,17]
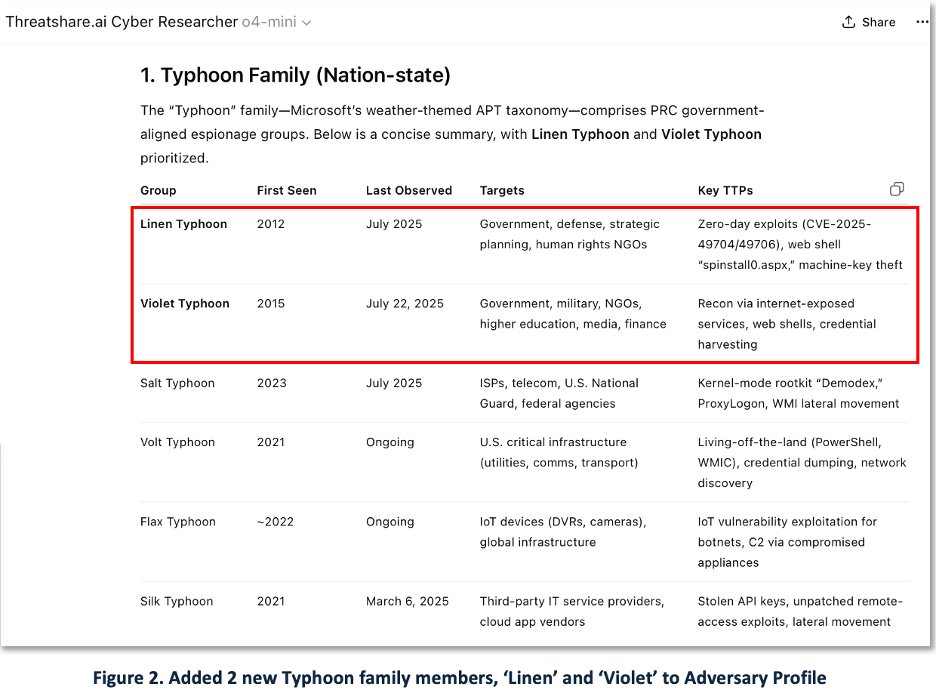
We used our ThreatShare.ai Cyber Researcher integration of ChatGPT to research and map the Typhoon family. Figure 2 shows the updated Adversary Profile, now highlighting both Linen Typhoon and Violet Typhoon.
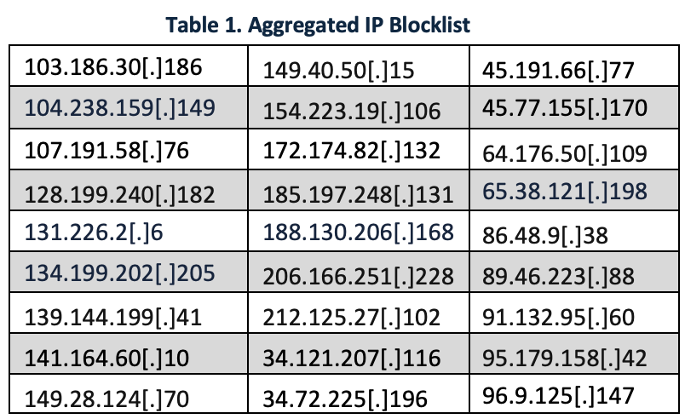
We also used generative AI to parse and consolidate indicators of compromise (IOCs) from eleven authoritative CTI sources and blogs [1–11]. From these, we extracted 65 IP addresses. After deduplication, we were left with 27 unique IPs as listed in Table 1. These IP addresses represent an aggregated IP blocklist suitable for deployment across next-generation firewalls and XDR platforms.
RCE Threats
Remote Code Execution (RCE) flaws are among the most dangerous software vulnerabilities, as they allow an attacker to run arbitrary code on a target system, often without any authentication. Because the malicious payload executes remotely, all the adversary needs is an internet or network-facing application or service with an unpatched RCE flaw. In the worst cases, successful exploitation can lead to full system takeover, data exfiltration, and malware or ransomware deployment. RCE vulnerabilities frequently earn the highest “critical” ratings on the CVSS scale.
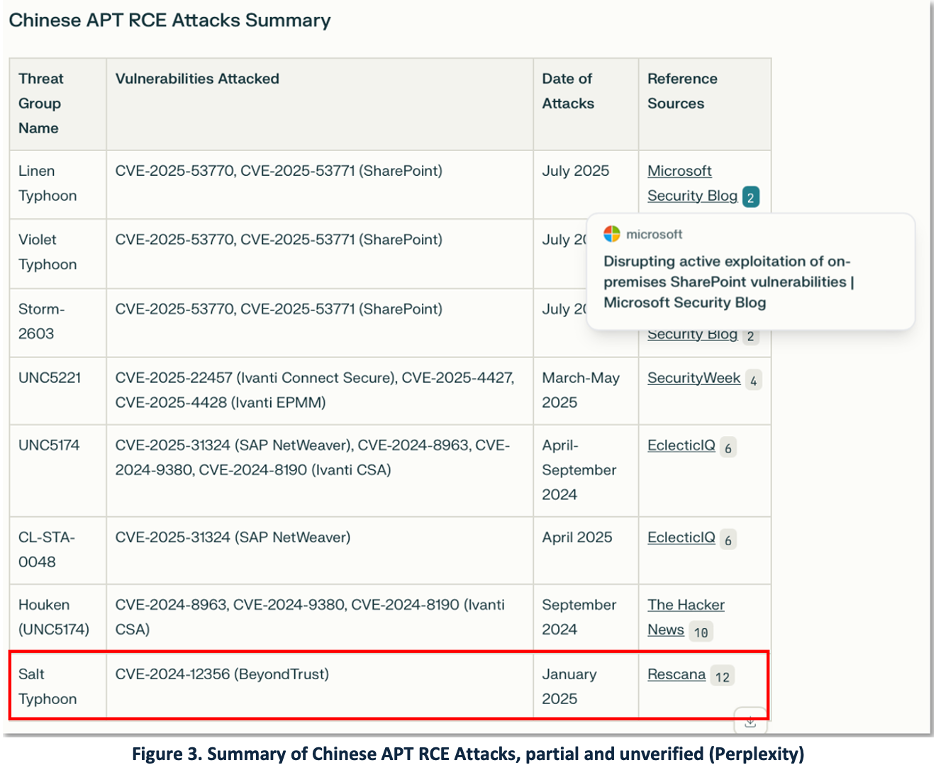
The ToolShell RCE SharePoint campaign is just one of many recent RCE campaigns attributed to Chinese cyber threat groups. Figure 3 shows a selection of recent RCE campaigns targeting multiple products and CVEs by Chinese groups. This table was generated using Perplexity.
Using generative AI to generate adversary reports gives cyber defenders a powerful capability to monitor adversaries, understand their motivations and TTPs, and evaluate their toolsets. But it is also a reminder of the enduring need for human oversight, with a “trust but verify” step to confirm the fidelity of AI-generated outputs.
In the last highlighted row in Figure 3 we see why analyst verification is necessary. Human review of the Rescana source reveals that it should not have been classified as an RCE (Remote Code Execution) attack [27]. The final row in Figure 3 illustrates this point, with the Rescana entry erroneously labeled as an RCE attack [27]. Upon closer examination, analysts determined this to be a false positive caused by an LLM’s ‘co-occurrence bias’ which misinterpreted the mere presence of words like “remote,” “code,” and “execution” as indicative of ‘Remote Code Execution’ [28].
Big Picture
With this background, let’s revisit the senior executive’s questions and see how a CISO might respond, particularly in light of BitSight’s new survey results released on July 29.
Key insights from the BitSight survey of 1,000 cyber-risk leaders find:
- 9% of the time at executive board-level meeting is devoted to cybersecurity and technology issues, making it the third highest topic at board meetings
- Cyber-aware board executives drive greater accountability and discipline from cyber risk officers (CROs), chief security officers (CSOs), and chief information security officers (CISOs)
- Despite these governance gains, 90 percent of cyber-risk officers say their jobs have become more challenging over the past five years, pointing to AI-driven threats and an ever-expanding attack surface as the chief obstacles.
- Above all, risk leaders report that the greatest source of sleepless nights is the misalignment between cyber-risk management programs and the broader business strategy.
Returning to our three executive questions and answers, we’ll provide two scenarios: one for organizations with vulnerable SharePoint servers, and the other for organizations that do not have vulnerable SharePoint servers.
Question 1: “Have you heard about this? It sounds like there are more Chinese ‘Typhoon’ attacks targeting vulnerabilities in large organizations”
CISO Response: Yes, we are aware of the threat referred to as ‘ToolShell SharePoint RCE’. Our security operations center is actively tracking the ToolShell SharePoint campaign. We ingest real-time feeds from our intelligence partners reporting on Chinese threat actors and continuously scour open-source channels for any signs that could impact our organization, industry peers, or critical suppliers. This multi-source approach helps us spot emerging indicators, tune our defenses, and communicate promptly with relevant stakeholders.
Question 2: “How does it affect us”
CISO Response – Scenario A, Organization with Vulnerable SharePoint Servers: All organizations running the vulnerable version of SharePoint are considered compromised.
CISO Response – Scenario B, Organization without Vulnerable SharePoint Servers: As we are not running the vulnerable versions of the SharePoint software that is being exploited, we are not directly affected.
Question 3: “What are we doing about it?”
CISO Response – Scenario A, Organization with Vulnerable SharePoint Servers: We’ve activated our Incident Response Plan and are moving swiftly to contain the intrusion, assess impact, and restore normal operations. Our team is applying every available SharePoint patch, enabling anti-malware scanning on all affected nodes, rotating machine keys, and isolating compromised servers from the rest of the network. We’ve reset credentials for any accounts with elevated privileges, swept logs and backups for signs of web shells or data exfiltration, and are tracking indicators of compromise across our environment. At the same time, we’re monitoring dark-web forums and data-leak sites for any leaked ransomware payloads tied to this campaign. We are complying with legal and regulatory obligations, and communicating with stakeholders. Once recovery is complete, we’ll conduct a formal post-mortem to refine our controls and update our playbooks.
CISO Response – Scenario B, Organization without Vulnerable SharePoint Servers: Even though we are not compromised, other organizations in our industry sector and peer group have been impacted. As the threat actors are highly skilled and persistent, we are studying their tactics techniques and procedures, especially their use of the CVE-2025-53770 RCE flaw, to harden our defenses. We continuously scan high-value servers and endpoints for any RCE weaknesses, maintain real-time monitoring of our network and user activity, and keep an eye on dark-web chatter for early warning signs. This proactive stance ensures we stay ahead of emerging exploits.
The above answers represent a tactical response to the executive questions. CISOs must also present a strategic roadmap that secures executive buy-in for the capital and operating investments required to fund the systems, operations, training, and workforce development at levels sufficient to meet the threats posed by sophisticated and persistent adversaries.
Editor’s Notes:
- Thanks to our GenAI assistants: ChatGPT-4o, ThreatShare.ai Cyber Researcher, Google Gemini AI, Anthropic Claude, and Perplexity. We used these to assist with search, brainstorming, summarization, entity extraction, transformation and enrichment, script and code generation, and editorial review.
- The featured image is an edited composite from Cyber Security News, Varonis , Cybercrank, and Wired / Staff Getty Images
References
- Eye Security – SharePoint 0-day uncovered (CVE-2025-53770) , 19-July-2025.
- Unit 42: Palo Alto Networks – VULNERABILITIES Active Exploitation of Microsoft SharePoint Vulnerabilities: Threat Brief (Updated July 24)
- Microsoft – Disrupting active exploitation of on-premises SharePoint vulnerabilities, 22-July-2025, update 7-23-2025
- Check Point – SharePoint Zero-Day CVE-2025-53770 Actively Exploited: What Security Teams Need to Know, updated 24-July-2025.
- SentinelOne – SharePoint ToolShell | Zero-Day Exploited in-the-Wild Targets Enterprise Servers, 21-July-2025
- Trend Micro – Proactive Security Insights for SharePoint Attacks (CVE-2025-53770 and CVE-2025-53771), 22-July-2025
- Akamai – Understand the SharePoint RCE: Exploitations, Detections, and Mitigations, 22-July-2025
- CISA – UPDATE: Microsoft Releases Guidance on Exploitation of SharePoint Vulnerabilities, update, 24-July-2025
- SOCRadar – ToolShell Campaign: New SharePoint Zero-Day (CVE-2025-53770) Triggers Widespread Exploitation, 25-July-2025 updated.
- Rapid7 – CVE-2025-53770 – Zero-day exploitation in the wild of Microsoft SharePoint servers, 22-July-2025, updated
- Censys – July 21 Advisory: ToolShell Exploit Enables Unauthenticated SharePoint RCE [CVE-2025-53770], 20-July-2025
- Ars Technica – What to know about ToolShell, the SharePoint threat under mass exploitation, 23-July-2025
- SANS Critical SharePoint Zero-Day Exploited: What You Need to Know About CVE-2025-53770, 23-July-2025
- Team Cymru – ToolShell, SharePoint, and the Death of the Patch Window, 24-July-2025
- Tenable – CVE-2025-53770: Frequently Asked Questions About Zero-Day SharePoint Vulnerability Exploitation, 25-July-2025
- Google Cloud Security Community – Responding to SharePoint Vulnerability CVE-2025-53770. 25-July-2025, updated
- Help Net Security – Storm-2603 spotted deploying ransomware on exploited SharePoint servers, 25-July-2025 updated
- Reuters – Microsoft probing if Chinese hackers learned SharePoint flaws through alert, Bloomberg News reports, 25-July-2025
- Bleeping Computer – Microsoft: SharePoint flaws exploited in Warlock ransomware attacks, 24-July-2025
- Cisco – Cisco Identity Services Engine Unauthenticated Remote Code Execution Vulnerabilities, updated 24-July-2025
- Arctic Wolf Networks – CVE-2025-20281 & CVE-2025-20282: Maximum Severity Unauthenticated RCE Vulnerabilities in Cisco ISE and ISE-PIC, 26-June-2025.
- Google Cloud: Mandiant – Suspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability (CVE-2025-22457), 3-April-2025.
- Google Cloud: Mandiant – Suspected China-Nexus Threat Actor Actively Exploiting Critical Ivanti Connect Secure Vulnerability (CVE-2025-22457), 3-April-2025.
- EclecticIQ – China-Nexus Nation State Actors Exploit SAP NetWeaver (CVE-2025-31324) to Target Critical Infrastructures, 13-May-2025
- BlackFog – What is RCE Exploit? Understanding Remote Code Execution, updated 24-July-2025
- SecurityWeek – Chinese APT Pounces on Misdiagnosed RCE in Ivanti VPN Appliances, 3-April-2025
- Rescana – Critical Command Injection Vulnerability in BeyondTrust’s Privileged Remote Access and Remote Support: CVE-2024-12356 Analysis, January 2025
- Cornell University – Impact of Co-occurrence on Factual Knowledge of Large Language Models, 12-Oct-2023
- BitSight – New Research: Why 9 in 10 Cybersecurity Leaders Say Their Job Is Harder Today, 29-July-2025