In our last CISO Advisor, the CISO answered a CEO request for strategic intelligence. Here, it’s the CISO who issues an RFI to the Cyber Threat Intelligence (CTI) team for a tactical intelligence request for an update on the Lazarus Group, a DPRK (North Korea) threat actor.
The tasking was triggered by a Sept 4 SentinelLABS OSINT report detailing Lazarus campaigns against job-seekers and crypto exchanges/service providers, building on earlier public warnings from Google Mandiant and U.S. government agencies.
This brief shows how to apply the AIA model – Awareness, Impact, Act – to a tactical CTI update:
- Awareness. Collect and enrich relevant open-source intelligence (OSINT) to map actors, campaigns, motives, techniques, indicators, and infrastructure.
- Impact. Assess implications for large enterprises in critical infrastructure sectors, with emphasis on cryptocurrency, financial services, and technology.
- Act. Deliver a tailored counter-threat plan, with examples and prioritized measures.
Bottom line. What initially seemed like a quick read-through evolved – as CTI RFIs often do – into a much larger thread pull. Analysis across ~3 years of related OSINT exposed a dense web of linked personas, indicators, infrastructure, and campaigns. The team assesses Lazarus as agile, persistent (active since at least 2009), audacious, financially motivated and fear-driven, with a track record ranging from crypto-exchange theft to exploitation of SWIFT-connected banking operations. With proven and practical CTI methods and tools, boosted with assistive GenAI (Generative AI), the team updated the actor’s modus operandi and is implementing tactical countermeasures (defensive controls, threat hunting, proactive takedowns, training). The CISO plans a follow-up brief for senior leadership on strategic ramifications and next steps.
Awareness
A CISO RFI to CTI kicks off scoping, source review, and synthesis action. For this tasking, analysts reviewed 21 primary sources, extracted indicators and findings, and aggregated them into a working set for enrichment and hunting (see References and Action sections for examples).
With remote tech work on the rise, DPRK-sponsored operators deploy fake IT workers who impersonate non-DPRK nationals to gain employment and privileged access across industry sectors country borders. Objectives include funds/cryptocurrency theft and espionage. Operators mine social media, careers sites, and job boards; use GenAI to build convincing personas and assistance in interviews; stand up front companies; and register look-alike domains to impersonate hiring firms, service providers, and job candidates.
With that background, the following factors make this a complex RFI:
- Threat Actor: The Lazarus Group is not a single threat actor; rather it is a dynamic cluster of actors conducting both state-sponsored and financially motivated operations.
- Campaigns: The reports describe multiple campaigns and operations – ‘Contagious Interview’ (AKA ClickFake) and ‘Wagemole ’ conducted from 2023 -2025 [6-9].
- Tradecraft: ClickFix and related lures deliver links/prompts that persuade applicants to execute commands under the guise of tests or troubleshooting [1,3,10-13].
- Persistence and scale: ThaiCERT reports more than 180 operations attributed to Lazarus Group from 2009 – 2025 [9].
Adversary Profiles (context for analysts)
In CTI tradecraft, Adversary Profiles provide essential context, describing: actor motives, targeting preferences, victimology, TTP (Tactics, Techniques, and Procedures), known infrastructure, malware and tools, and campaign histories. Foundational sources for understanding and developing adversary profiles include MITRE ATT&CK, which includes Lazarus Group and its subgroups [8], and ThaiCERT which provides a searchable catalog [9].
DTEX recently published a detailed report on DPRK’s Cyber Syndicate and Hidden IT Workforce [7]. At a strategic level, the report finds that the DPRK is a “more sophisticated and dangerous cyber actor than widely recognized”, functioning like a state-sanctioned crime syndicate with profits from ransomware, cryptocurrency theft, financial fraud, and stolen intelligence funding weapons development, state espionage, and nuclear and military programs. At the tactical level, we are interested in key ‘Mission Areas’ including AI, Crypto, Espionage, Surveillance, and IT Workers. The Crypto Mission, which is most pertinent to our report and explored later, provides campaign details of four subgroups. A companion DPRK report provides email indicators ‘Spotting Malicious Remote IT Applicants’.
Campaigns Analysis (2023–2025 highlights) [1–15]
- The campaigns primarily target workers and companies in the cryptocurrency and IT sectors.
- The Contagious Interview campaign (AKA ClickFake) surfaced publicly in Nov-2023 (Palo Alto Networks Unit 42) and again in Sept-2025 (SentinelLABS in Sept-2025) [1,6].
- The campaigns targeted job applicants in the cryptocurrency industry with the intent to gain access to their systems, collect intelligence, and steal cryptocurrency assets and privileged accounts.
- Sekoia notes CeFi (Centralized Finance) exchanges and service providers as primary targets [3]. Reuters reports impersonation of crypto firms and exchanges (e.g., Bitwise, Robinhood, Kraken) using recruiter domains and LinkedIn personas [15].
- Operators monitored CTI/security services to assess C2 exposure and quickly rotate infrastructure; use of Validin to vet new assets illustrates rapid redeployment post-takedown [2].
- SentinelLABS reported at least 230 victims, largely cryptocurrency professionals.
Impact
The impact from this threat is severe, varied, and tangible:
- Direct financial theft: DPRK-linked operations have produced multi-billion losses; Bybit $1.5B in 2025; Axie/Ronin $625M in 2022; DMM Bitcoin ~$308M in 2024 [7, 12].
- Espionage & data loss: Long, post-compromise dwell time enables persistent access and exfiltration across defense, energy, finance, government, and technology sectors, with malware like InvisibleFerret enabling persistent C2 connections [13].
- Operational friction: Enterprises incur material costs for incident response, hardening, tabletop exercises, and re-engineering HR/Talent workflows to vet remote applicants and vendors.
- Platform and brand damage: Job boards, recruiting services, and crypto platforms are impersonated or abused, degrading trust.
- Individual harm: Job seekers and contractors face device compromise, credential theft, and crypto-asset loss from fake recruiters/front companies and ClickFix-style lures.
Action
This section provides:
- Examples for CTI-led playbooks.
- Mitigation recommendations from a prioritized roll-up of recent CTI research and advisories.
- Working practices and tips for pragmatic methods that reduce analyst overload.
Examples
The CTI community benefits from both commercial and open-source intelligence, but coverage is uneven and naming varies across vendors (the same actor often has multiple aliases). While automated sharing exists (STIX/TAXII, MISP, IODEF, vendor APIs), no universal standard has emerged. In practice, CTI teams still need reliable ways to extract indicators, enrich context, and share beyond raw CSVs. Ad-hoc GenAI prompts plus vendor intel can accelerate that workflow.
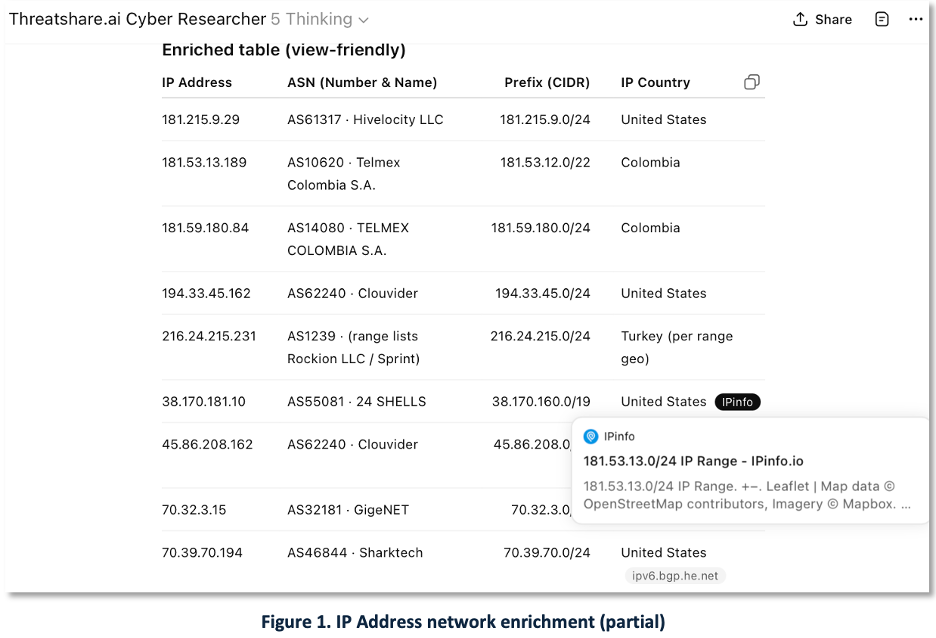
The sources referenced in this report provide hundreds of network and file-based indicators. Many reports contain a simple list of IP addresses with no additional context. Figure 1 — IP list enrichment: Starting from a plain list of IPs, our tailored ChatGPT (ThreatShare.ai Cyber Researcher) does look-ups of ASNs, prefixes, and countries to provide more context and make indicators actionable for blocking, hunting, and scoping.
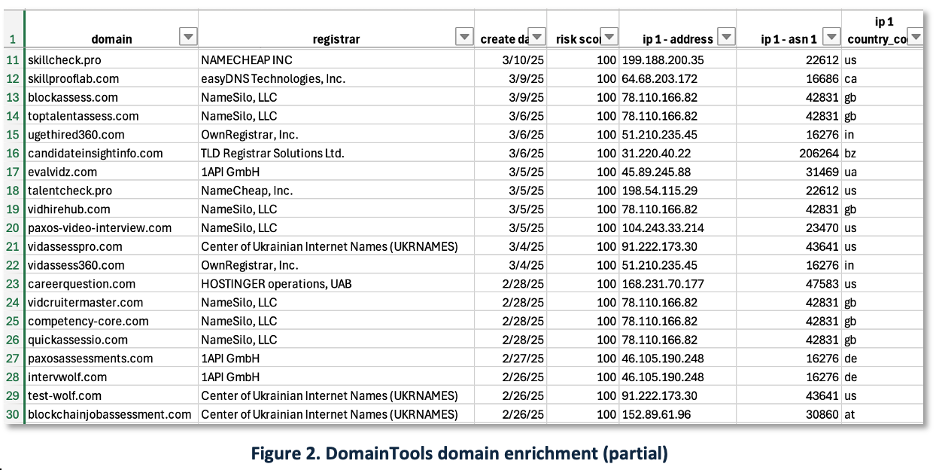
Figure 2 — Domain & network enrichment. DomainTools Iris provides WHOIS, DNS, network enrichment, and hosting pivots. Similar DNS intelligence is available from Validin and Silent Push. From a list of single IPs, these systems turn data into usable intelligence.
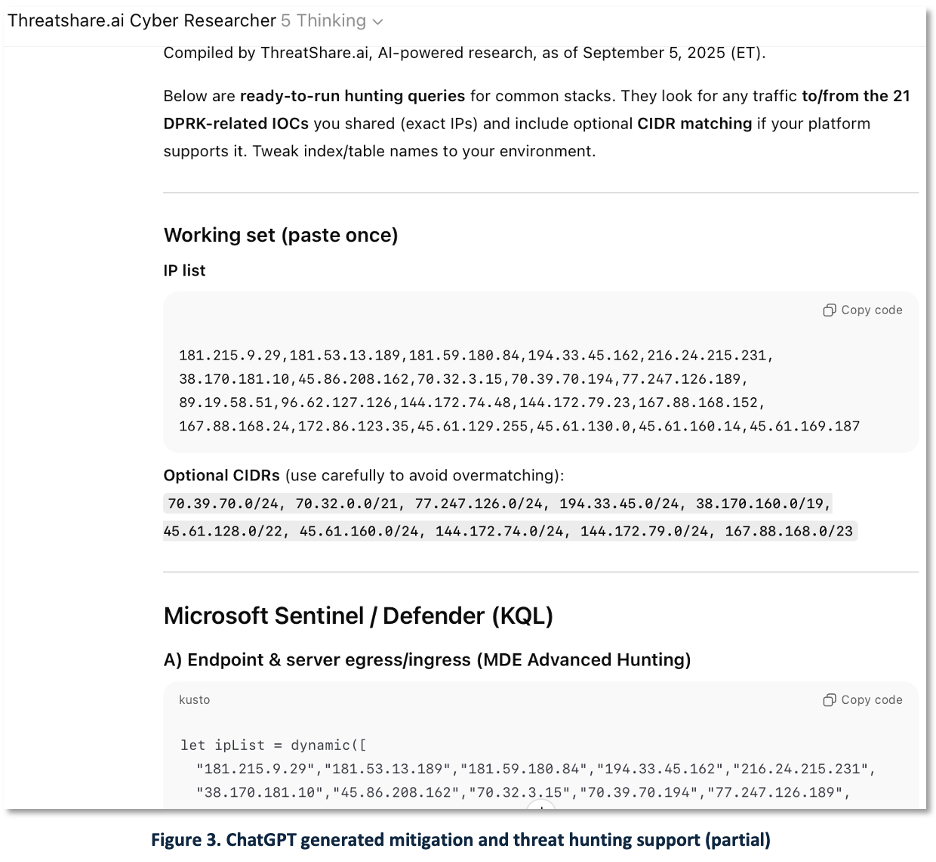
Figure 3 — Hunt query generation. Using the enriched indicators, GenAI can generate ready to run threat-hunting queries ready for SIEM, EDR, network devices, Splunk and other defensive systems, shortening the time from intel to detection.
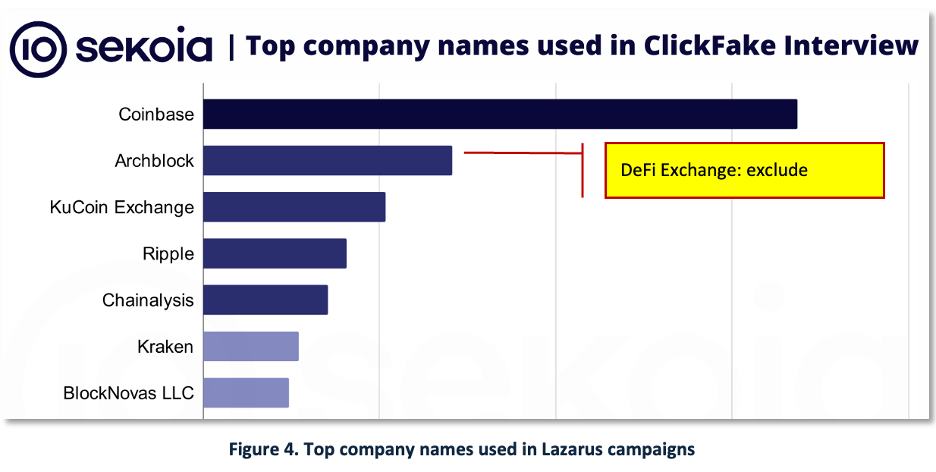
Figure 4 — CeFi lure brands. From Sekoia, we extracted Centralized Finance (CeFi) exchange/service names used in recruiter-lure campaigns. These brand terms inform proactive controls and monitoring.
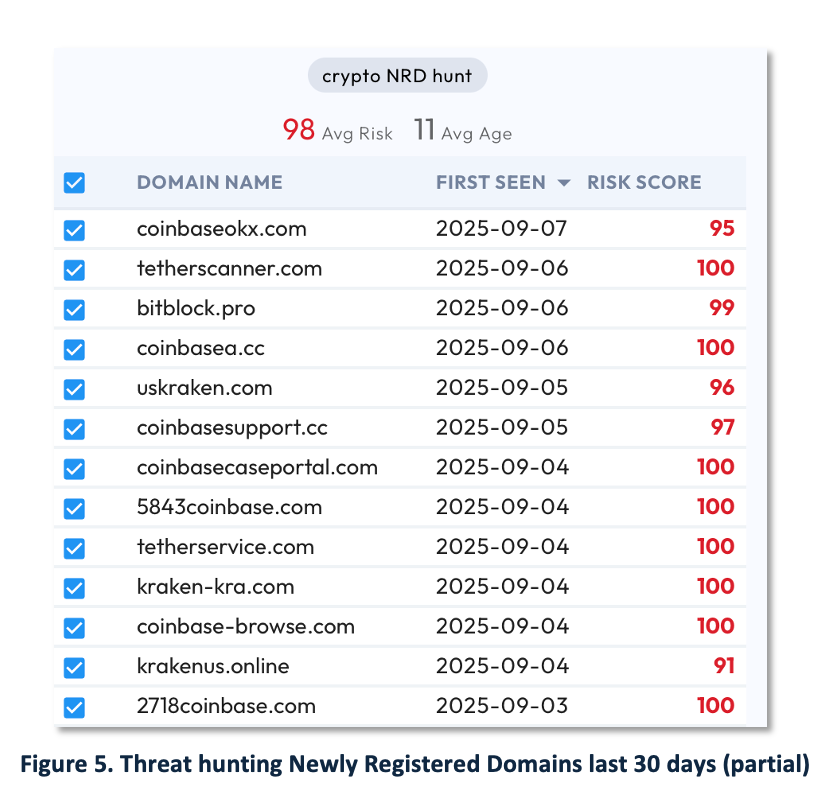
Figure 5 — Newly registered domain (NRD) watch. On September 7 we set NRD monitors for some of the Sekoia terms in DomainTools for ‘last-30-day’ registrations with ‘risk score > 90’. Results (partial) show ‘average risk 98’ and ‘age 11 days’, supporting the observation that adversaries rapidly rotate infrastructure and seed replacements after takedowns. Validin and Silent Push provide similar capabilities.
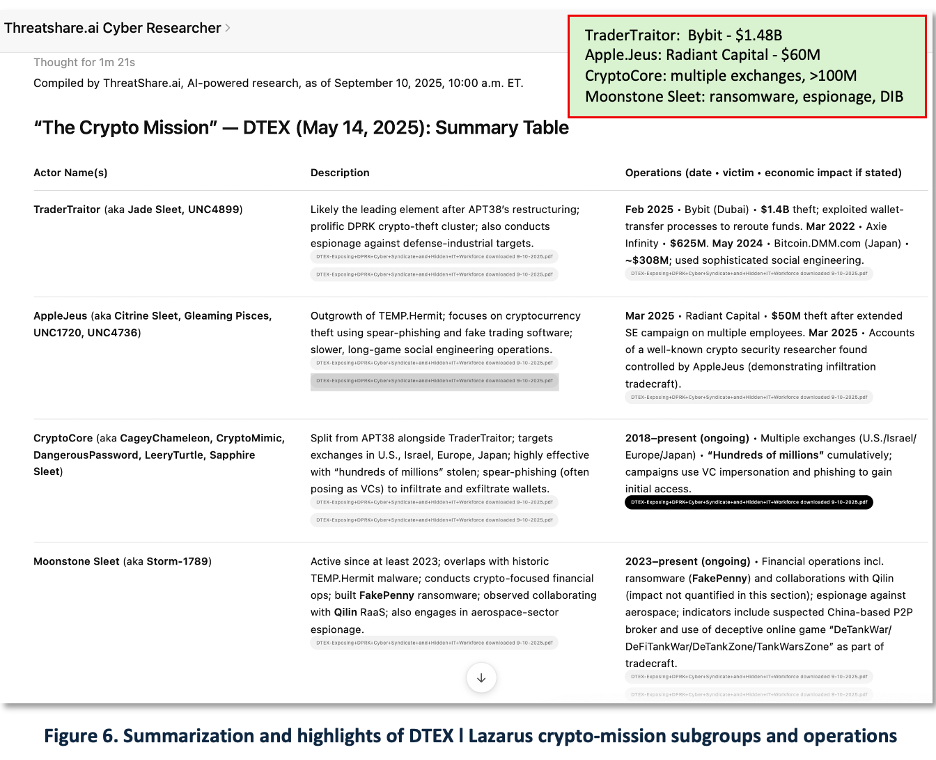
Figure 6 — Actor and campaign summarization. GenAI summarizes three pages of narrative text from the DTEX ‘Crypto Mission’ into a table. As noted below in the Google-Forrester survey, information overload is a serious problem for CTI teams. The ability to reduce hundreds of pages of reporting to a single table addresses a pressing need. It also facilitates generating content for executive briefings.
Countermeasures
Below is a concise roll-up of countermeasures drawn from the cited research and advisories.
SentinelLABS / Validin:
- Emphasize human factors and the role of infrastructure providers; crypto-sector job seekers should treat unsolicited recruiting and “assessment” links as high risk.
- Talent acquisition and career platforms should invest in proactive threat hunting and domain intelligence to watch brand terms, track infrastructure risk, and coordinate takedowns/seizures.
DTEX:
- Pre-employment: use camera-on interviews with anti-cheat controls, verify geolocation, and coordinate closely with HR.
- Post-employment: monitor remote access and endpoints; review email/messaging where engagement signals are low or anomalous.
- CTI operations: maintain up-to-date behavioral indicators and email IOCs linked to DPRK tradecraft.
Sekoia:
- Proactively schedule threat-hunting ops using current campaigns and lures.
- Use DNS intelligence to detect new fake interview sites and staging/C2 infrastructure.
Palo Alto Networks / Unit 42:
- Developers: scrutinize GitHub accounts with a single sparse repository or recent activity spikes.
- Applicants: independently verify that the company and role exist before engaging in tests or running tools.
- Enterprises: deploy shared IOCs across EDR, cloud, and next-gen firewalls.
SlowMist (eight recommended measures) [4]:
- Secure proxy configuration
- DNS traffic protection
- Network/host monitoring & threat detection
- Network segmentation & isolation
- System hardening
- Endpoint visibility & EDR
- Centralized log management & analysis
- Security awareness (phishing + blockchain-related risks)
Community coordination:
- Partner with national CERTs and sector ISACs to share indicators, accelerate takedowns, and align incident response across organizations.
CTI Team Overload
CTI teams must avoid the ‘perfect answer’ trap. GenAI excels at search and summarization, but unchecked ‘pull-the-thread’ work can spiral – burning cycles without improving decisions. A recent Google-Forrester survey of 1,500+ IT and security leaders echo this: the sheer volume of threats and data, plus analyst shortages, keeps many programs reactive. The fix is AI-assisted correlation at scale – backed by clear priorities and skilled human review – to turn intel into action.
Practical ways to stay proactive:
- Set PIRs and time-boxes. Define Priority Intelligence Requirements and limit research sprints.
- Triage for impact. Score by mission relevance and business impact; filter noise.
- Use GenAI with guardrails. Summarize, classify, and cluster; require sources, confidence tags, and human validation.
- Automate action. Feed enriched intel to SIEM/EDR/TIP/EASM systems.
- Define “stop” conditions. End thread-pulls when novelty drops (e.g., fewer new IOCs).
- Operationalize, measure, learn. Convert findings into playbooks and detections; track coverage and false-positive rates.
- Mind data and ethics. Avoid sensitive pastes; test for prompt injection; log decisions.
And speaking of a ‘fix,’ here’s a quick nod to the classic 80’s rock hit from The Fixx – ‘’One Thing Leads to Another’. It provides an apt and fun reminder that in CTI, one thread does indeed lead to another ad infinitum, so set stop-conditions before you chase. Check it on your favorite music source!
References
- SentinelLABS – Contagious Interview | North Korean Threat Actors Reveal Plans and Ops by Abusing Cyber Intel Platforms, 4-Sept-2025
- Validin – Lazarus Group Bybit Heist: C2 forensics, 11-March-2025, updated 12-July-2025
- Sekoia.io Blog | Threat Research & Intelligence – From Contagious to ClickFake Interview: Lazarus leveraging the ClickFix tactic, 31-March-2025
- SlowMist | Medium – Cryptocurrency APT Intelligence: Unveiling Lazarus Group’s Intrusion Techniques, 23-Feb-2025
- Safe{Wallet} Mandiant Preliminary Investigation – Article See new posts Conversation Square profile picture Safe.eth @safe Image Investigation Updates and Community Call to Action, 21-Feb-2025
- Palo Alto Networks: Unit 42 – Hacking Employers and Seeking Employment: Two Job-Related Campaigns Bear Hallmarks of North Korean Threat Actors 21-Nov-2023
- DTEX – Exposing DPRK’s Cyber Syndicate and Hidden IT Workforce, 14-May-2025
- MITRE ATT&CK – Lazarus Group
- ETDA (ThaiCERT) Threat Group Cards: A Threat Actor Encyclopedia
- Silent Push – Contagious Interview (DPRK) Launches a New Campaign Creating Three Front Companies to Deliver a Trio of Malware: BeaverTail, InvisibleFerret, and OtterCookie, 24-April-2025
- Proofpoint – Security Brief: ClickFix Social Engineering Technique Floods Threat Landscape , 18-Nov-2024
- Google | Mandiant: Staying a Step Ahead: Mitigating the DPRK IT Worker Threat, 23-Sept-2024
- ANY.RUN – Lazarus Group Attacks in 2025: Here’s Everything SOC Teams Need to Know, 10-Sept-2025.
- U.S. Federal Bureau of Investigation (FBI) – Alert Number: I-022625-PSA February 26, 2025, North Korea Responsible for $1.5 Billion Bybit Hack
- U.S. CISA, FBI, Treasury – Joint Advisory, Product ID: A22-108A: TraderTraitor: North Korean State-Sponsored APT Targets Blockchain Companies, 18-Feb-2022
- U.S. Department of the Treasury: Advisory – GUIDANCE ON THE DEMOCRATIC PEOPLE’S REPUBLIC OF KOREA INFORMATION TECHNOLOGY WORKERS, 16-May-2022
- Reuters – Exclusive: How North Korean hackers are using fake job offers to steal cryptocurrency, 4-Sept-2025
- Google Cloud Blog – Too many threats, too much data, say security and IT leaders. Here’s how to fix that, 28-July-2025
- Tech Monitor – Fake IT workers are making it tougher for companies to hire , 11-Sept-2025 https://www.techmonitor.ai/technology/cybersecurity/remote-hiring-cybersecurity?cf-view
- Chainalysis – What the Huione Group Shutdown Signals About the Future of Crypto Scam Infrastructure, 19-May-2025
- Chainalysis – The 2025 Global Adoption Index: India and the United States Lead Cryptocurrency Adoption, 2-Sept-2025
- Straits Research – Cryptocurrency Exchange Platform Market Size (2025-2033), published after February 2025
Editor’s Notes
This post was conceived, drafted, and reviewed by human cybersecurity analysts. We used ThreatShare.ai Cyber Researcher, ChatGPT, Google Gemini AI, Anthropic Claude, and Perplexity as GenAI assistants for brainstorming, search, summarization, entity extraction, transformation and enrichment, script and code generation, and editorial review. We also used GenAI to create the Featured Image.