Updated 6-Dec-2025. See Postscript for additional Cyber Threat Intelligence reporting since the original post on 5-Dec-2025.
In prior CISO Advisor posts we emphasized strategic intelligence. This edition shifts to tactical intelligence with a Flash Alert on CVE-2025-55182 (‘React2Shell’), a maximum-severity (CVSS 10) unauthenticated RCE (Remote Code Execution) flaw affecting the React Server Components (RSC) “Flight” protocol used by React and JavaScript frameworks that implement RSC, such as Next.js.
Our user scenario assumes a Managed Security Services Provider (MSSP), or an ISAC (Information Sharing and Analysis Center), serving enterprise customers in critical infrastructure sectors. The CISO needs a sector-level exposure report to guide triage and response.
This Flash Alert follows the ThreatShare’s AIA (Awareness, Impact, Action) model as detailed in the sections below.
Bottom line:
- CVE-2025-55182 (React2Shell’) is a critical unauthenticated RCE vulnerability in the React Server Components (RSC) “Flight” protocol used to accelerate JavaScript performance. As an embedded service, React2Shell is an example of supply chain risk.
- Preliminary ThreatShare analysis indicates >130,000 U.S. internet-facing hosts across ~1,000 organizations matching React technology in Shodan facets, with ~ 98% registered to cloud/hosting providers. Note these are potential exposures from OSINT and do not confirm vulnerable RSC versions.
- The vulnerability is easy to exploit, requiring only a crafted HTTP request. Exploit code is publicly available.
- Patches are available. Update immediately to 19.0.1, 19.1.2, or 19.2.1.
Awareness
The first disclosures and initial opensource intelligence reports of an RCE (Remote Code Execution) vulnerability in the React Server Flight protocol were reported on 3-Dec-2025 [1-8] .
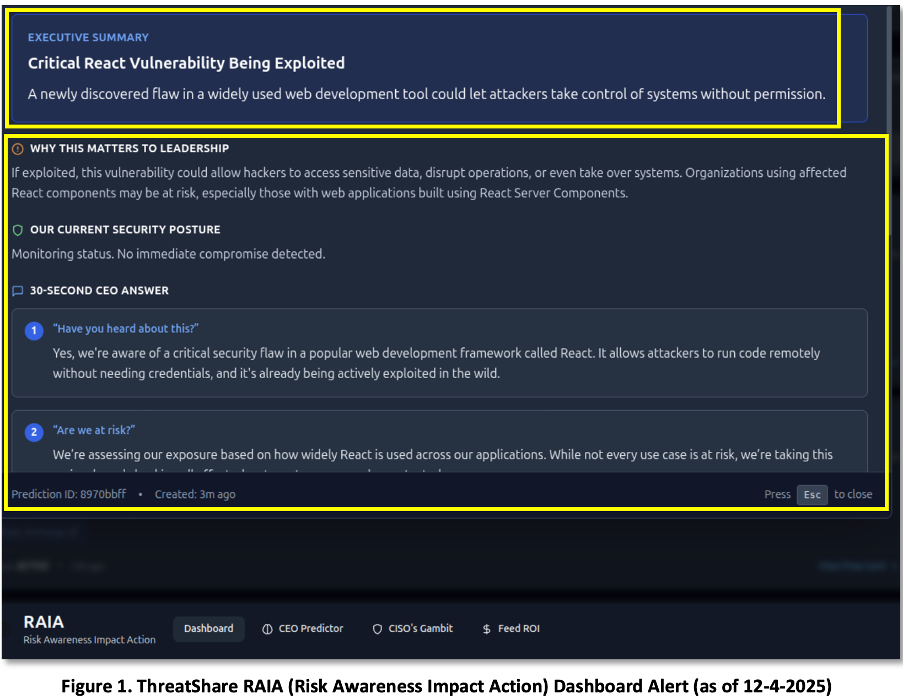
ThreatShare’s RAIA (Risk Awareness Impact Action) Cyber Threat Intelligence (CTI) platform alerted the CTI team on 4-Dec-2025 (Figure 1).
OSINT Summary:
- The React Server Flight protocol is embedded in web apps to improve the rendering speed of JavaScript and content.
- OXsecurity reports that the vulnerability affects the React and Next.js ecosystems, which power millions of active websites globally, including major platforms built with React such as Instagram, Netflix and Airbnb that serve billions of users daily [3]. This does not assert those platforms are vulnerable, only that the ecosystem footprint is large [3].
- WIZ Research reports 39% of cloud environments contain vulnerable instances [5].
Impact
In our use-case scenario, the CISO of a large MSSP serving the U.S. market needs to gauge customer exposure by industry sector to prioritize outreach, patching, and monitoring.
Using Shodan, the analyst identified >130,000 U.S. internet-facing hosts associated with React-based stacks. This provides a starting point, not proof that each host is running affected versions of React Server Components (RSC) – 19.0, 19.1, and 19.2.
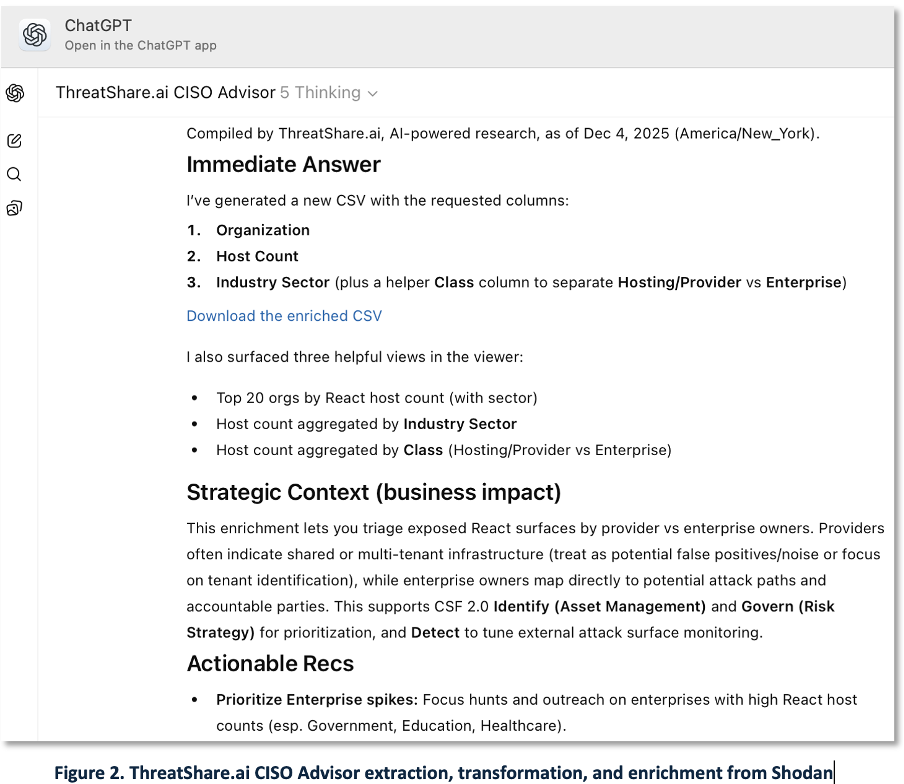
Next the analyst needed to assess the impact by sector. To expedite this, the analyst used GenAI to enrich the raw Shodan data with industry sectors using a simple industry classification taxonomy. Figure 2 shows how the Analyst used GenAI, in this case the ThreatShare.ai CISO Advisor implementation of ChatGPT Pro, to generate a script and a CSV that provided the sector classification enrichment for each of the 130,000 hosts.
This sector enrichment analysis gives the CISO a sense of the scale and distribution of potential exposure, indicating a heavy skew toward cloud/hosting providers and a significant tail across enterprise sectors.
Action
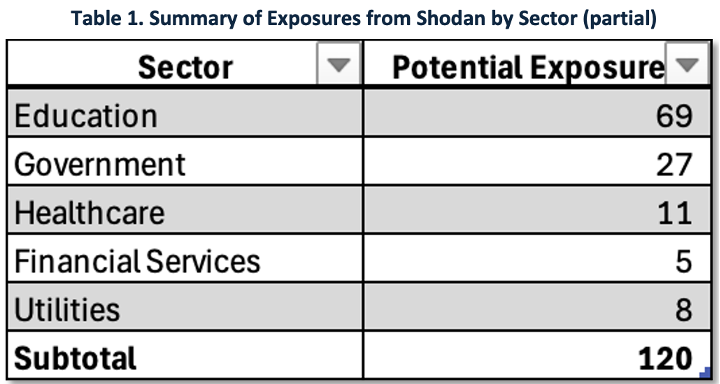
The CISO’s priority is to focus first on enterprise customers in critical infrastructure sectors with the highest host counts (Gov/EDU/Health/FS). The analyst has generated a priority target list for follow-up of 120 potential exposures across five key sectors, as summarized in Table 1. This enriched data set provides the MSSP with the intelligence needed to validate each instance and initiate mitigation steps.
Postscript
Since the original post on 5-Dec-2025, our OSINT feeds have surfaced new intelligence on exploitation in the wild and mitigations.
GreyNoise reported opportunistic, largely automated exploitation attempts of CVE-2025-55182 (React2Shell), adversary TTPs, and shared indicators of compromise (IOCs), including 81 IP addresses that defenders can use for blocking [9].
Amazon reported China-nexus cyber threat groups rapidly exploit React2Shell vulnerability (CVE-2025-55182), adversary TTPs, and shared indicators of compromise (IOCs), including 4 IP addresses that defenders can use for blocking [10].
Censys reported observations of more than “2.15 million instances of internet facing services that may be affected by this vulnerability, including exposed web services using React Server Components and exposed instances of frameworks such as Next.js, Waku, React Router, and RedwoodSDK. Note that this number reflects exposures of affected software but does not filter for vulnerable versions; as such, not all of these are necessarily vulnerable.” [11]
Cloudflare rolled out new React protections for customers of Cloudflare’s Web Application Firewall (WAF) [12].
Palo Alto Networks – Unit 42 identified over 968,000 React and Next.js instances in their telemetry, shared threat hunting queries, warned of heightened data exfiltration, and noted the enduring trade-offs between performance and security in system design. In React2Shell, React optimized data fetching and search engine optimization (SEO) to the detriment of moving the “attack surface closer to organizations’ most sensitive and valuable data” [13].
Editor’s Notes
This post was conceived, drafted, and reviewed by human cybersecurity analysts. We used ThreatShare’s RAIA Platform for detection, analysis and alerting, and ThreatShare.ai’s CISO Advisor customized ChatGPT assistant for script generation and extraction, transformation, and enrichment of data from Shodan. We used multiple chatbots as research and editorial assistants. The research was informed by sources listed in the Reference section. The Featured Image is sourced from WIZ.
References
- React Team – Critical Security Vulnerability in React Server Components, 3-Dec-2025
- Vercel | NEXT.js – Security Advisory: CVE-2025-66478, 3-Dec-2025
- OXsecurity – Millions of servers vulnerable to RCE in React Components, 3-Dec-2025
- Tenable – CVE-2025-55182: Frequently Asked Questions About React2Shell: React Server Components Remote Code Execution Vulnerability, 3-Dec-2025
- Wiz – Critical Vulnerabilities in React and Next.js: everything you need to know, 3-Dec-2025
- AWS – CVE-2025-66478: RCE in React Server Components, 4-Dec-2025
- Ars Technica – Admins and defenders gird themselves against maximum-severity server vuln, 3-Dec-2025
- TechSpot – Critical vulnerability in React JS framework has a near 100% chance to be exploited, 4-Dec-2025
- GreyNoise – CVE-2025-55182 (React2Shell) Opportunistic Exploitation In The Wild: What The GreyNoise Observation Grid Is Seeing So Far, 5-Dec-2025
- AWS – China-nexus cyber threat groups rapidly exploit React2Shell vulnerability (CVE-2025-55182), 4-Dec-2025
- Censys – December 5 Advisory: Unauthenticated RCE Flaw in React Server Components [CVE-2025-55182], 5-Dec-2025
- Cloudflare – Cloudflare WAF proactively protects against React vulnerability, 3-Dec-2025
- Palo Alto Networks – Unit 42: Critical Vulnerabilities in React Server Components and Next.js, 4-Dec-2025.