This edition of CISO Advisor addresses a common executive concern about commercial Cyber Threat Intelligence (CTI). Here’s the issue as expressed by a notional CISO from a large financial services company with 2,000 plus employees.
‘Our CTI team spends more than $500K a year for 20 External Threat Intelligence Service Providers (ETISPs), plus open sources and internal telemetry. Leadership wants to redirect funding toward GenAI and agent initiatives and has asked us to cut ETISPs from 20 to 10. We know some sources overlap, but we don’t know which. The challenge is consolidating without weakening our security posture.’
This post explores how CISOs can respond to consolidation directives while defending CTI value. We first test the concern, then shift the conversation from cost to outcomes, using ThreatShare’s AIA (Awareness, Impact, Action) model, as follows:
- Awareness. The CISO’s problem statement surfaces difficult questions about CTI program metrics, stakeholders, and value, for which there is no definitive answer. SANS recommends tying CTI metrics to business outcomes and use-cases, cautioning that poorly chosen metrics can add overhead [1]. Another SANS survey reports a 19-point increase (from 33% to 52%) in executive participation in defining CTI requirements [2], while Recorded Future reports 43% of cybersecurity leaders use CTI for strategic planning [8]. BCG (Boston Consulting Group) projects ~ 10% + in budget increase across all cyber categories, with 80% citing AI-powered cyberattacks as their top concern [3].
- Impact. Preliminary GenAI-assisted analysis of static IOCs (Indicators of Compromise) of the same ransomware campaign from 4 ETISP sources, found no overlap in coverage. While these findings may be surprising, they should be considered anecdotal pending more rigorous testing.
- Action. As CTI benefits both executives and technical staff, CISOs should prioritize investments in CTI program management and threat hunting. For CTI program management, the Cyber Threat Intelligence Capability Maturity Model (CTI-CMM) is a proven and practical tool that helps CISOs balance CTI investments across stakeholder domains [4]. CISOs should also prioritize investments in threat hunting, which provides the behavioral indicators from internal sources essential for combatting advanced and automated espionage and exfiltration attacks.
Bottom line: CTI is a critical input to AI-enabled defense, providing the enrichment and context needed to counter cyberattacks. The onset of automated agent attacks like the recent Chinese nation-state espionage campaign reported by Anthropic makes the need for effective CTI even more urgent [18]. CISOs should ensure their CTI program balances strategic, operational, and tactical needs across all stakeholders. CTI-CMM is a management tool that helps CISOs plan, measure, and govern a balanced and effective CTI program. Intelligence-driven threat hunting is essential for combatting the most advanced threats.
Awareness
The volume and pace of attacks and news related to Cybersecurity and GenAI creates acute overload and situational awareness challenges. As the accountable executive, the CISO must keep teams aligned, inform senior leadership, and partner with peers across the enterprise and industry. CISOs rely on their domain experience, trusted human sources, multiple news and market intelligence feeds, and GenAI assistants and agents to provide situational awareness.
Figure 1 illustrates ThreatShare’s CISO Advisor as a strategy and market-intelligence assistant.
Selected highlights from this Nov 3 report and recent updates:
Organizations subscribe to ~26 paid commercial threat-intelligence feeds on average, per Forrester [12].
Recorded Future executive survey [8]:
- 91% plan to increase CTI spending.
- 81% plan to consolidate vendors in 2026.
- 76% spend $250K+ per year on ETISPs (excluding services).
- 14% spend $1M+ per year.
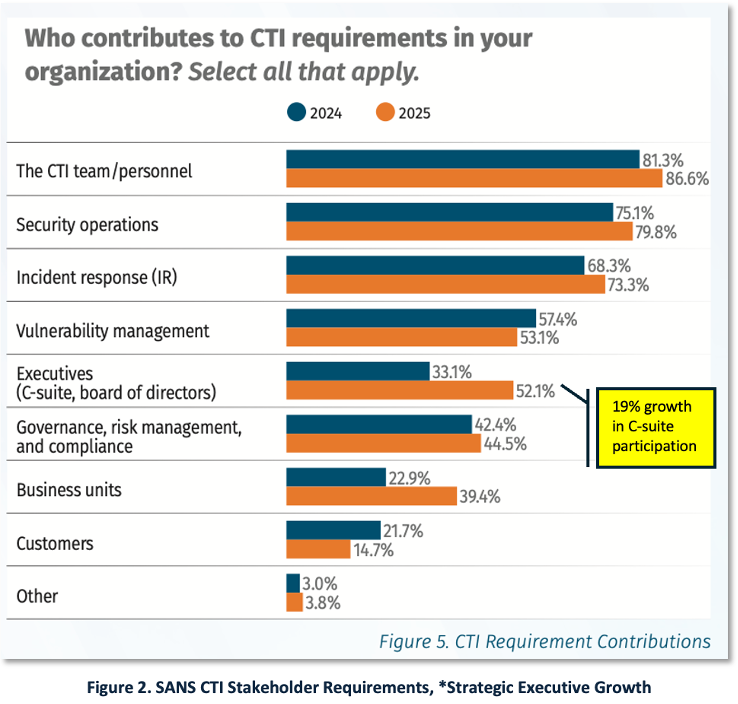
Survey findings from SANS show broad and rising support for CTI across stakeholder groups, strengthening the CISO’s budget case [2]. Figure 2 highlights contributors both within the security organization (SOC, IR, Vulnerability Management) and outside it (GRC, business units). Perhaps most significant, executive participation increased ~19 percentage points (33% to 52%), indicating greater strategic use of CTI at the leadership level.
Impact
Identifying duplicative ETISP sources is challenging given variation in CTI types, indicator classes, and stakeholder needs. Below are three consolidation-analysis cases a mature CTI team can pursue.
Case 1 – Atomic Indicators Test: In CTI, atomic indicators (domains, URLs, IPs, hashes, registry keys) are static, ephemeral artifacts. They are easy for SOC/IR teams to deploy for containment and blocking, provide direct evidence of activity, but have limited value for threat hunting without behavioral context.
On 31-October-2025 we tasked GenAI assistants to find OSINT reports from the prior 30 days where multiple ETISPs covered the same campaign. The assistants returned 9 reports across 3 campaigns. For a preliminary test, we selected 4 sources (Cisco Talos, Trend Micro, Huntress, ThreatLocker) reporting on the Qilin ransomware campaigns for the period, Oct 22 – 26 (Figure 3) [13-16].
We then asked the assistants to extract network indicators (domain names, IPs). After basic normalization, we observed 48 unique IOCs with no cross-source overlap. This suggests that removing any one source might reduce awareness for this campaign. Caution: observations from a small-sample snapshot are anecdotal and not generalizable.
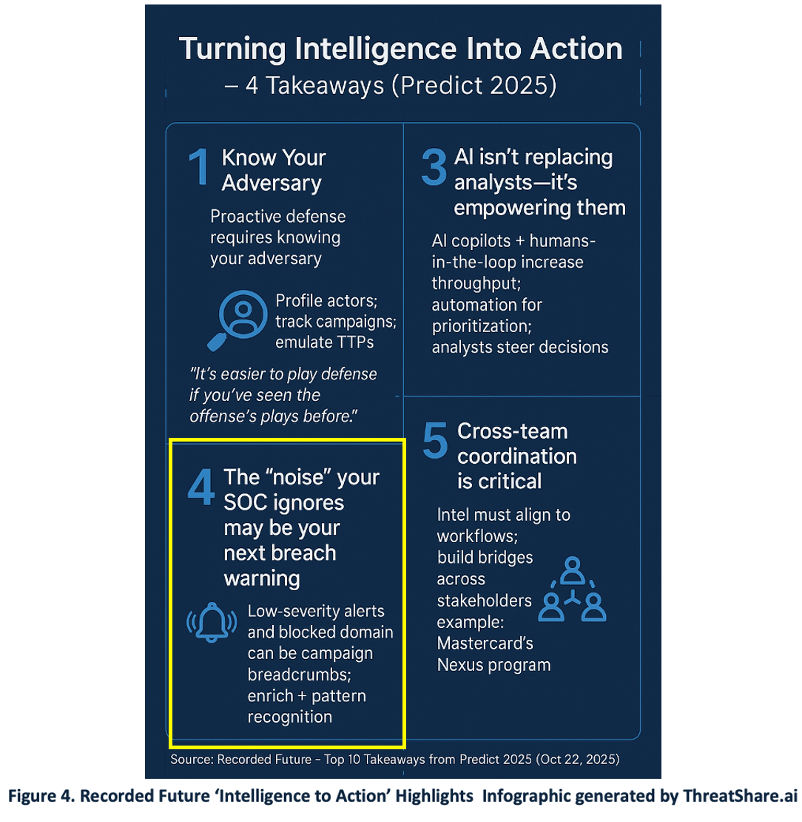
Case 2 – Noise vs Breadcrumbs: Our prompts also surfaced Recorded Future’s “Top 10 Threat Intelligence Insights” (Figure 4) [9]. Takeaway # 4 caught our attention – The “noise” your SOC ignores may be your next breach warning). To assist the CISO briefing, we asked our assistant to generate an infographic summarizing a 2,400 word narrative. (Figure 4).
For consolidation, some duplication is expected. If a feed is nearly 100% overlapping with others and rarely adds timeliness or context, it is a candidate for reduction. However, uncertain overlap can negate savings if cuts increase missed detections. Consolidation decisions should weigh overlap, timeliness, precision, and added context, not just indicator counts.
Case 3 – CTI for Threat Hunters: We reviewed CTI requirements for hunting from Intel471 [5 , 6] and Recorded Future [9]. While the cyber threat intelligence analyst and threat hunt analyst disciplines are complementary and even converging, they involve distinct methods, sources, tools, analytic techniques, and skills. For example:
- Threat hunting is human-led, hypothesis-driven, grounded in internal telemetry, and seeks behavioral/TTP patterns and anomalies. Advanced adversaries using living-off-the-land (LOTL) tactics can evade IOC-only detection, making intelligence-driven behavioral hunting essential.
- CTI analysts teams integrate external reporting and campaign context, primarily focusing on atomic indicators, malware and TTP analysis.
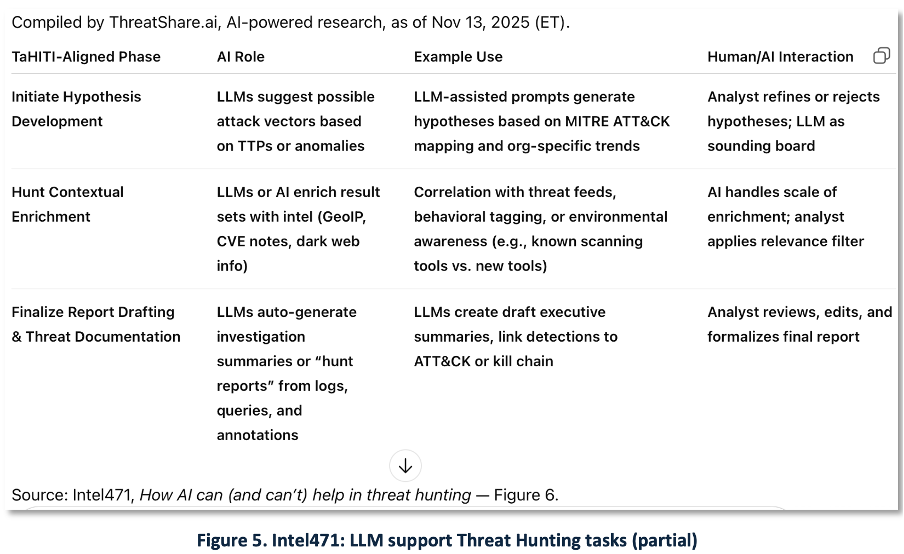
In current practice, LLM deployments are mostly assistive, not autonomous; analysts remain in the loop. LLMs assist a subset of hunting phases – for example, hypothesis generation, enrichment/summarization, and reporting – as reflected in our summary of Intel471’s TaHiTI model for tactical threat hunting (Figure 5).
Implications for consolidation: Anthropic’s report of automated agentic AI attacks will likely spur development and deployment of AI (ML and LLMs) assistants and agents for cyber defenders. For CTI, CISOs should prioritize providers that improve behavioral coverage, context, and timeliness for hunters and responders, not just raw IOC volume. Where two sources are duplicative on IOCs but diverge on TTP depth, retain the one with higher utility to investigations.
Action
CISOs can draw on several open resources to assess, improve, and benchmark CTI programs.
Measurement frameworks: Forrester provides quantitative and qualitative metrics based on the CART model – Complete, Accurate, Relevant, Timely – to evaluate actionable threat intelligence and demonstrate value to stakeholders [12]. In addition, vendor tools like Recorded Future’s Threat Intelligence Maturity Assessment offer free benchmarks.
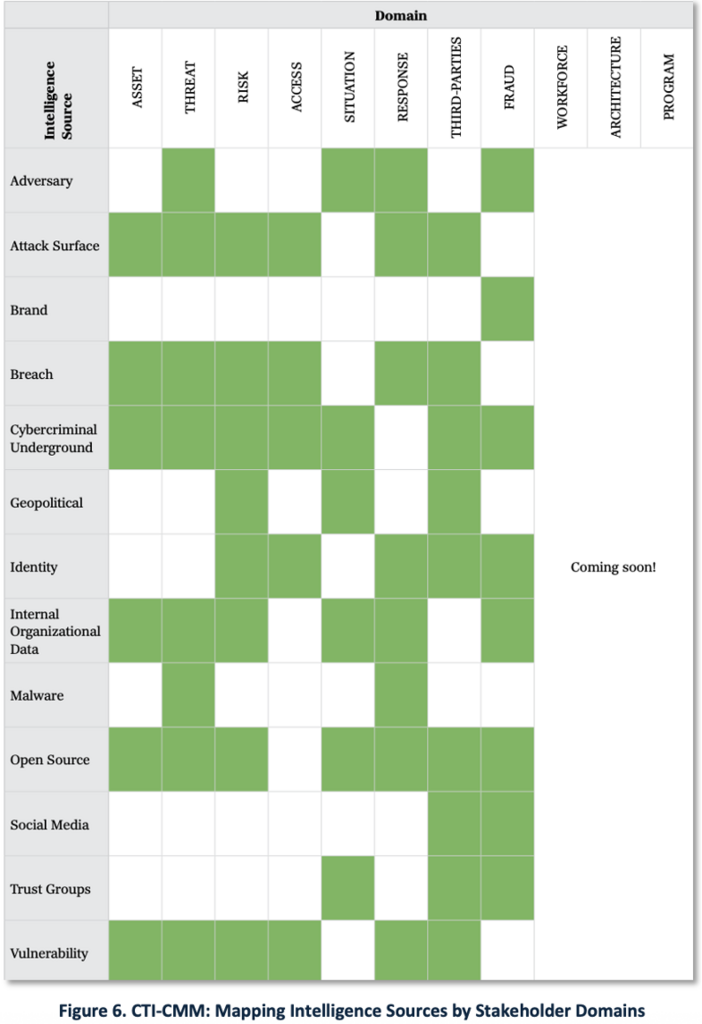
Capability model: The Cyber Threat Intelligence – Capability Maturity Model (CMM) is a leading, community-driven, vendor-neutral framework derived from DOE C2M2 [4, 5]. As shown in Figure 6, CTI-CMM maps 13 source types across 11 domains (applications). Each domain includes four maturity levels—Pre-Foundational, Foundational, Advanced, and Leading (not shown). Today, CTI-CMM is a periodic self-assessment which organizations use to structure improvements and track progress over time. The CMM model provides a means for CISOs to define metrics based on stakeholder value.
Organizations can combine CART metrics with CTI-CMM domains to define stakeholder-centric measures, set target maturity levels, and prioritize investments. This approach supports consolidation decisions by focusing on demonstrable stakeholder value rather than raw feed counts, and it creates an auditable record for governance and continuous improvement. In a combined implementation, CTI-CMM focuses on program maturity across 11 domains, while CART focuses on the quality of the CTI product itself.
Threat Hunting: As noted, behavioral indicators are required to combat the most advanced adversaries that use TTP like LOTL which is impervious to indicator-based CTI. CISOs should evaluate both threat hunt managed services as well as internal threat hunt team options.
Outlook
The Chinese nation-state automated attacks are a watershed event. Defenders should anticipate more frequent and more autonomous adversary activity, and accelerate AI-enabled defenses.
CTI teams should maintain focus on stakeholder value, continuously assessing the quality of their intelligence for Completeness, Accuracy, Relevance, and Timeliness (CART).
Effective assisted/automated defense will require:
- High-quality, comprehensive CTI feeding enrichment, detections, and playbooks.
- Investment in both cyber threat analysts and threat hunters, including internal teams and managed services.
- A skilled workforce trained to use AI tools responsibly and to validate outputs.
- Governance and regulations that enforce model risk management, privacy, and auditability.
- Deception and deterrence capabilities integrated with detection/response.
- International and industry cooperation to share indicators, TTPs, and lessons learned.
Editor’s Notes
This post was conceived, drafted, and reviewed by human cybersecurity analysts. We used ThreatShare.ai Cyber Researcher, ChatGPT, Google Gemini AI, Anthropic Claude, Anthropic Sonnet, and Perplexity as GenAI assistants as sounding boards for brainstorming, search, summarization, entity extraction, transformation and enrichment, script and code generation, and editorial review.
References
- SANS – Beyond Meh-trics: Examining How CTI Programs Demonstrate Value Using Metrics, 9-Jan-2025
- SANS – 2025 CTI Survey, May 2025
- BCG (Boston Consulting Group) – AI Creates New Cyber Risks. It Can Help Resolve Them, Too, 30-July-2025
- CTI-CMM, V1.2 – Cyber Threat Intelligence – Capability Maturity Model, 10-Sept-2025
- Cisco Talos – Maturing the cyber threat intelligence program, 10-Sept-2025
- Intel471 – How AI can (and can’t) help in threat hunting, 9-Sept-2025
- Intel471 – Six Key Takeaways From the SANS 2025 Threat Hunting Survey, 26-March-2025
- Recorded Future – Introducing the 2025 State of Threat Intelligence Report: Threat Intelligence Shifts from Defense to Strategy, Nov 12, 2025
- Recorded Future – Top 10 Takeaways from Predict 2025: Turning Intelligence Into Action, published 22-Oct-2025
- Recorded Future – Threat Hunting vs Threat Intelligence, Nov 10, 2025
- Verizon Data Breach Investigations 2025 Report (DBIR) , April 2025.
- Forrester – How To Measure The Effectiveness And Value Of Threat Intelligence, 10-Dec-2024
- Cisco Talos – Uncovering Qilin attack methods exposed through multiple cases, 26-Oct-2025
- Trend Micro – Agenda Ransomware Deploys Linux Variant on Windows Systems Through Remote Management Tools and BYOVD Techniques, 23-OCT-2025
- Huntress – Looking Through a Pinhole at a Qilin Ransomware Attack, 22-Oct-2025
- ThreatLocker – Qilin RaaS group: Technical analysis, from initial access to beaconing, 26-Oct-2025
- NIST SP 800-61r3 – Incident Response Recommendations and Considerations for Cybersecurity Risk Management
- Anthropic – Disrupting the first reported AI-orchestrated cyber espionage campaign, November 2025
- Google Threat Intelligence – Preparing for Threats to Come: Cybersecurity Forecast 2026, 4-Nov-2025
- Mastercard – How payment threat intelligence helps banks fight fraud faster , 6-Nov-2025
- SC Media – The rise of compensation-linked consequences following a breach, 7-Nov-2025.
- Microsoft – The 5 generative AI security threats you need to know about, 30-Oct-2025