Five days ago, we reported on cyber risks to the electric power sector from rogue communication devices embedded in Chinese solar components. Since then, new threat intelligence has surfaced. In this Flash update, we spotlight two developments relevant to cybersecurity and third-party risk teams in the water, energy, and communications sectors.
Japan Joins Scrutiny of Chinese Solar Components
On May 23rd, the South China Morning Post (SCMP) reported that the Japanese government has launched an investigation into alleged rogue communications embedded in Chinese-manufactured solar panels used in the national grid [1]. While this move is notable, it largely echoes prior actions taken by the United States and European Union, following similar disclosures by Reuters and other outlets.
Zero-Day Exploits Target Utility Software
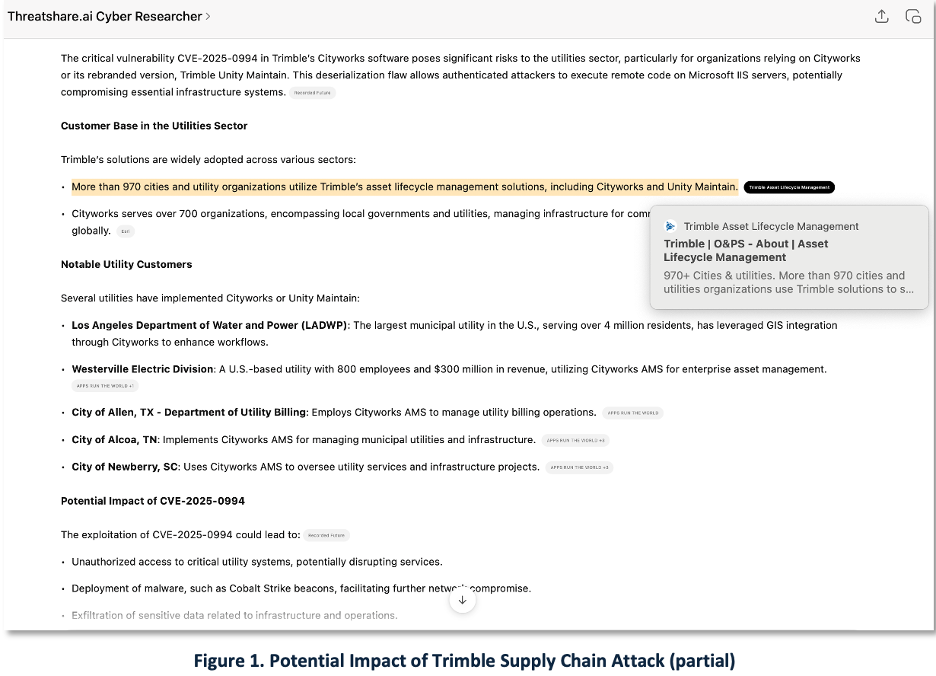
More significant is new research released May 22nd by Cisco Talos, which documents active exploitation of a zero-day vulnerability (CVE-2025-0994) in Trimble Inc.’s Cityworks software. The Chinese threat actor UAT-6382 has been linked to these attacks, which target critical infrastructure sectors — including water, energy, communications, and municipal governments. [2–7].
Cityworks, also marketed as Trimble Unity Maintain, is asset management software (AMS) widely used by state and local government-owned utilities. The vulnerability, a high-severity deserialization flaw, allows authenticated attackers to execute remote code on Microsoft IIS servers. This creates a foothold for deploying malware such as Cobalt Strike and VShell.
Measuring the Impact with GenAI
While Talos, Trimble, and Recorded Future provided technical IOCs and tactical threat context, they did not assess potential operational impact. Using our custom implementation of ChatGPT—ThreatShare.ai Cyber Researcher — we conducted an impact assessment based on Trimble’s own data. As shown in Figure 1, Trimble’s asset management platforms serve over 970 cities and utility organizations, impacting more than 80 million people.
GenAI for IOC Extraction and Normalization
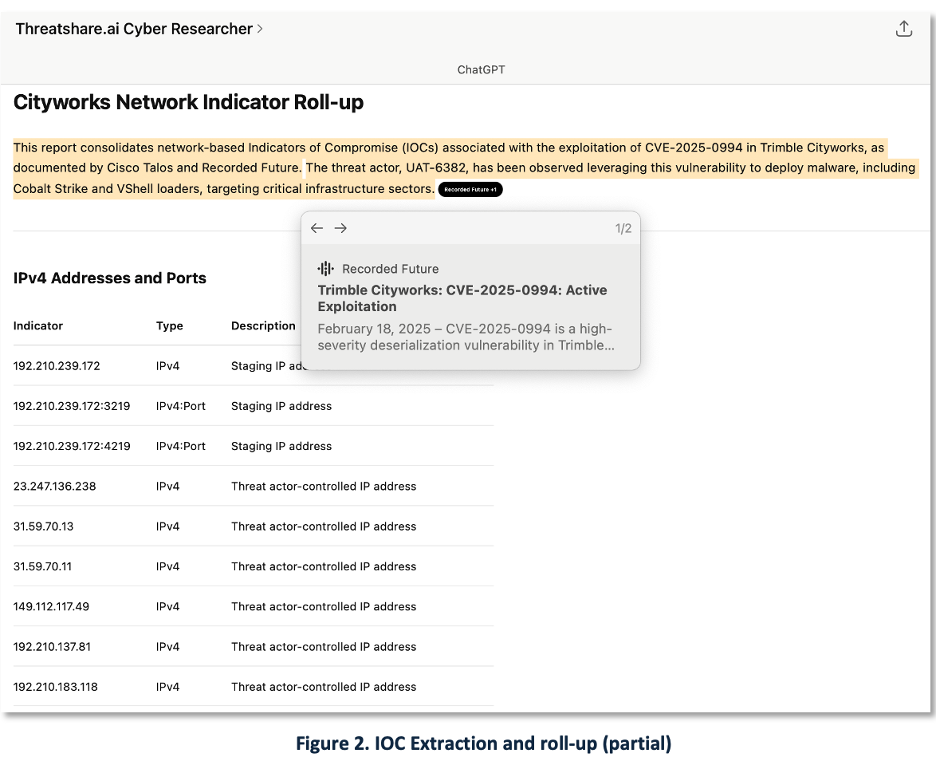
We also used GenAI to perform core Cyber Threat Intelligence (CTI) tasks. A common analyst workflow involves extracting and normalizing IOCs from mixed-source formats – PDFs, HTML, JSON, and CSV. Our system aggregated indicators from Cisco Talos and Recorded Future into a structured dataset. Figure 2 shows a partial view of the IOC roll-up. The process took several iterations, and while imperfect, the results were operationally useful.
The consolidated indicators—domains, IPs, and URLs—can be fed into threat detection and monitoring tools to identify related activity. Passive DNS tools such as Silent Push and DomainTools help contextualize indicators by showing historical resolutions, frequency of use, and first/last seen metadata. Tools like VirusTotal or CrowdStrike Falcon Hybrid Analysis add behavioral insight and malware attribution.
Summary and Recommendations
UAT-6382 is one of several Chinese state-aligned actors targeting U.S. and allied infrastructure. The exploitation of CVE-2025-0994 in widely deployed utility software highlights systemic third-party risk in the software supply chain.
Utilities, municipalities, and ISACs supporting these sectors must monitor for exploitation, patch vulnerable systems, and continuously update detection signatures. MSSPs should prioritize visibility into AMS platforms and OT-adjacent tools often overlooked in conventional IT security stacks.
GenAI technologies can assist by automating IOC processing, threat summarization, and real-time intelligence fusion — helping analysts stay ahead of fast-moving adversaries.
Editor’s Notes:
- Thanks to our GenAI assistants: ChatGPT-4o, ThreatShare.ai Cyber Researcher, Google Gemini AI, and Perplexity.
- Thanks for the featured image to securityonline.info: https://securityonline.info/critical-0-day-cityworks-flaw-actively-exploited-by-chinese-apt-uat-6382/
References
- SCMP (South China Morning Post) – Japan probes Chinese solar panels over hidden device fears, power disruptions, 23-May-2025
- Talos Threat Advisory – UAT-6382 exploits Cityworks zero-day vulnerability to deliver malware, 22-May-2025
- GitHub | Cisco-Talos-IOCs- https://github.com/Cisco-Talos/IOCs/blob/main/2025/05/uat-6382.txt , 22-May-2025
- RecordedFuture | TheRecord – Chinese-speaking hackers targeting US municipalities with Cityworks bug, 22-May-2025
- RecordedFuture | Insikt Group – Trimble Cityworks: CVE-2025-0994, 19-Feb-2025
- Trimble – Trimble Cityworks: CVE-2025-0994?, 6-Feb-2025
- Trimble – Overview
- CISA Alert Code: ICSA-25-037-04 – Trimble Cityworks (Update A), 11-Feb-2025
- Tenable – https://www.tenable.com/cve/CVE-2025-0994