As GenAI and cyber incidents dominate headlines, cyber threat intelligence (CTI) teams in large enterprises are seeing a sustained surge of requests for information (RFIs) from executives, colleagues, customers, and partners. It is a surge unlikely to abate.
RFIs are ad-hoc, time-bound, topic-specific intelligence asks. In the SANS 2025 CTI Survey, 70% of respondents say an increasingly complex digital landscape is reshaping CTI processes; 52% operate dedicated CTI teams; and 33% already use AI within CTI workflows. And while employment data shows an overall cooling in cybersecurity postings amid CSaaS/consolidation trends, postings for CTI roles analysts are up 14.2% [1-3].
This suggests increasing and enduring demand for experienced CTI analysts with GenAI and critical thinking skills who can create effective prompt dialogs, fuse internal and external sources, validate GenAI outputs, and brief decision-makers. This need inspires our RFI Desk concept – a blended consulting service designed for AI-assisted CTI research and reporting.
We illustrate the model with a representative executive RFI for an executive leadership briefing with a seven-day turnaround, which asks:
- ‘What are bulletproof hosters (BPH)?
- How could they impact our organization?
- What are we doing about it?’
Bulletproof hosters cater to cybercriminals, offering resilient, abuse-tolerant infrastructure that keeps malicious services online. The BPH threat has been documented for nearly two decades, yet remains a serious problem. [3–12]
Our use-case describes:
- Cybercrime Landscape: Cybercrime groups seek permissive providers of Internet infrastructure like domain name registrars, hosting companies, and BPH.
- Tools and Tips: Cyber defenders operate as a cyber neighborhood watch, sharing tools, data, and intelligence from open and proprietary sources.
- Enforcement Actions: Intelligence derived from these methods supports threat mitigation, takedowns, and law enforcement actions.
- Outlook: While the cybersecurity industry embraces GenAI to combat the threats, policies and laws governing cyber infrastructure and AI also need strengthening.
Cybercrime Landscape
The catalyst for this topic was a recent reporting from Silent Push on BPH networks [3, 19], which followed on prior work and sources, including:
- Our previous research on FIN7, Russian cyber groups APT29, Funnull (China-linked), and collaboration between Chinese Volt groups and front companies.
- Intel 471 coverage of sanctions on actors behind the BPH provider Zservers [5]
- DomainTools analysis of domain registrars, fast-flux, proxies, and BPH used in APT28/APT29 influence operations [6]
- KrebsonSecurity on Stark Industries as a global proxy/BPH network supporting cyberattacks and disinformation [7].
Why this matters for CTI: CTI investigations require an understanding of the scale, complexity, and features of the global cyber terrain. Selected features include:
- Governance: ~ 200 sovereign jurisdictions plus multistakeholder bodies and regulators with overlapping rules.
- Internet / Surface Web: Billions of routable IPs (IPv4+IPv6), allocated to more than 70,000 autonomous systems (ASNs), and announcing more than prefixes.
- Domain Names: More than 1,000 domain registries and 2,000 domain registrars involved in domain registrations; hundreds of millions of active domain names with estimates that 70% of new domain registrations are malicious or suspicious.
- Dark Web: Billions of leaked credentials and rising ransomware leak-site activity.
- Social Web and Messaging Platforms: Large ecosystems of cybercrime and crypto-fraud channels reaching millions of users.
The threat landscape spans cybercriminal, state-sponsored, hacktivist, and front-company ecosystems. While state-sponsored groups may receive the most attention from national security practitioners, Google Threat Intelligence Group notes that intrusions by cybercriminal groups outnumbered state-sponsored intrusions by a factor of 4 to 1. The collaboration among the various groups is another complicating factor. For example, Russian cybercrime and hacktivist groups are known to support state-sponsored operations like APT44/Sandworm [8].
Bulletproof hosting providers serve illicit actors by delivering uptime, resilience, anonymity, and anti-enforcement posture. These capabilities are delivered through advanced features like fast-flux DNS, proxy/redirector layers, WHOIS privacy, and rapid re-hosting across abuse-tolerant networks.
Silent Push and Spamhaus, two of the leading authorities on BPH networks, track approximately 80 and 400 BPH networks respectively. This may understate reality. Recorded Future reports that adversaries also abuse Legitimate Internet Services (LIS) – such as cloud/VPS, CDNs, registrars, email and comms platforms, and remote-admin tools – to blend in [9].
Tools and Tips
Domain Registrar and ASN/ISP Intelligence
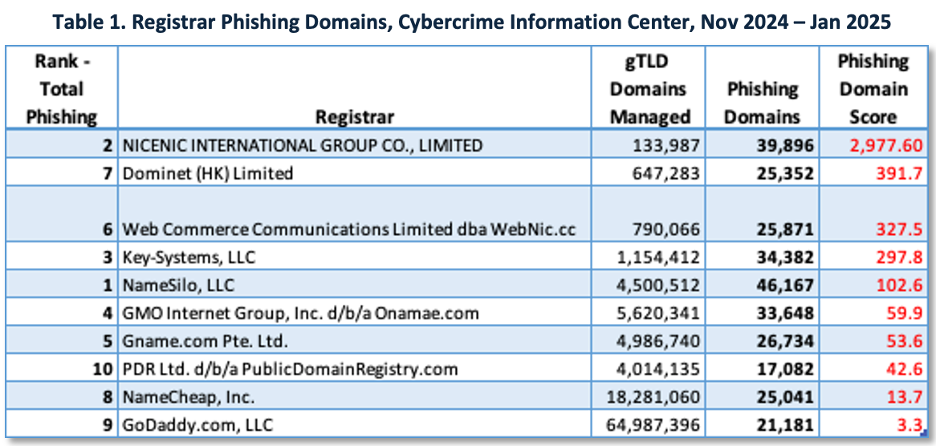
Cyber threat actors gravitate towards domain registrars with lax oversight. Table 1 ranks registrars by phishing-domain risk (Cybercrime Information Center).
Beyond registrar scoring, Akamai and Scamalytics, rate ASNs/ISPs for abuse risk.
Commercial DNS Intelligence platforms (e.g., Silent Push and DomainTools) provide search, monitoring, and automation for malicious domains/infrastructure – supporting brand protection, proactive hunting, takedowns, and law-enforcement workflows.
CTI Data Sources
CTI is a well-established, multi-billion-dollar market segment spanning commercial and community sources; many offer free/community tiers, and many OSINT projects offer paid upgrades. CTI spans threat data (indicators) and Internet topology. Representative sources we use:
- Threat Data: SANS – Internet Storm Center, Spamhaus, and AlienVault OTX – Open Threat Exchange(now LevelBlue)
- Internet Topology (Routing Data): Hurricane Electric BGP Toolkit, Cloudflare Radar, bgp.tools, Ipinfo, and Shodan.io
GenAI BPH Scenarios
These scenarios show how analysts can combine GenAI + OSINT + DNS intel to monitor BPH and answer RFIs – focusing on methods, not specific vendors. Most established cybersecurity and CTI vendors have or are in the process of implementing GenAI across their cybersecurity stacks. In large organizations security stacks could include as many as 80 tools from 25 vendors, with 25 paid threat feeds plus open source feeds. The workflows below apply regardless of where an organization is in their GenAI or platform consolidation.
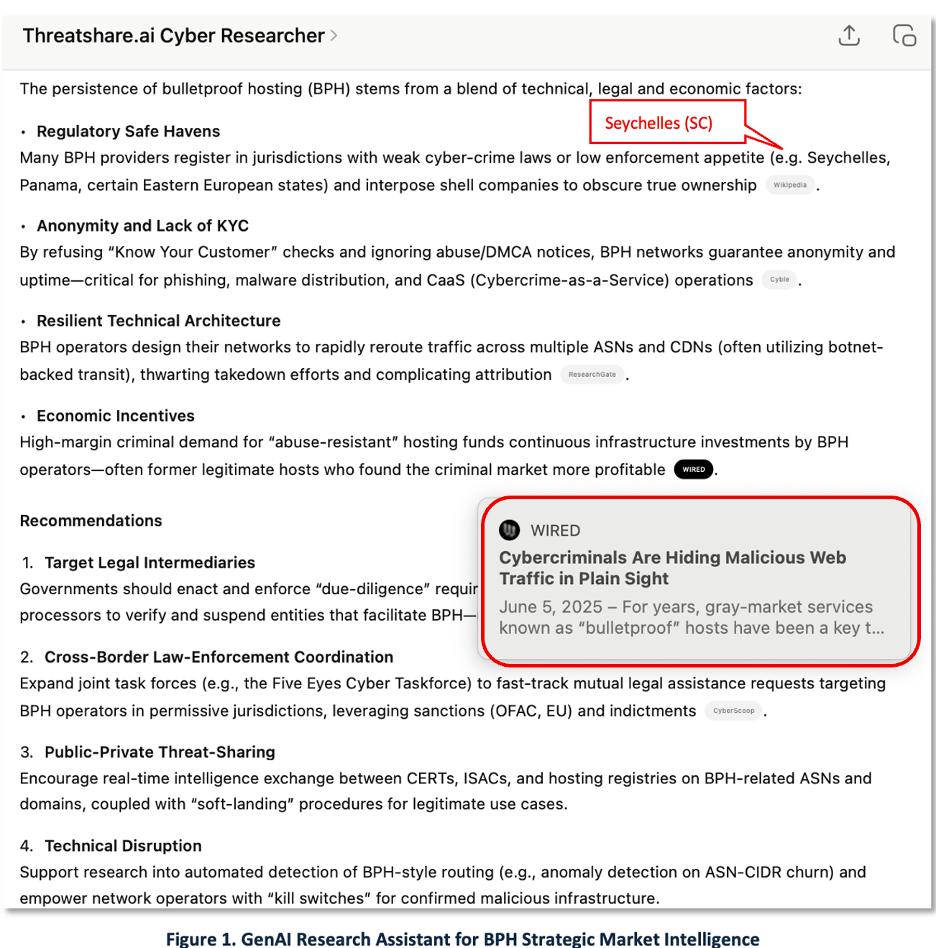
Our scenario starts with an analyst doing basic research on BPH using GenAI in support of an international law enforcement investigation. In Figure 1 we see a BPH overview report generated using our ‘ThreatShare.ai Cyber Researcher’ implementation of ChatGPT tailored for the cybersecurity domain. As highlighted, the analyst was intrigued by the Seychelles mention and the BPH report from Wired.
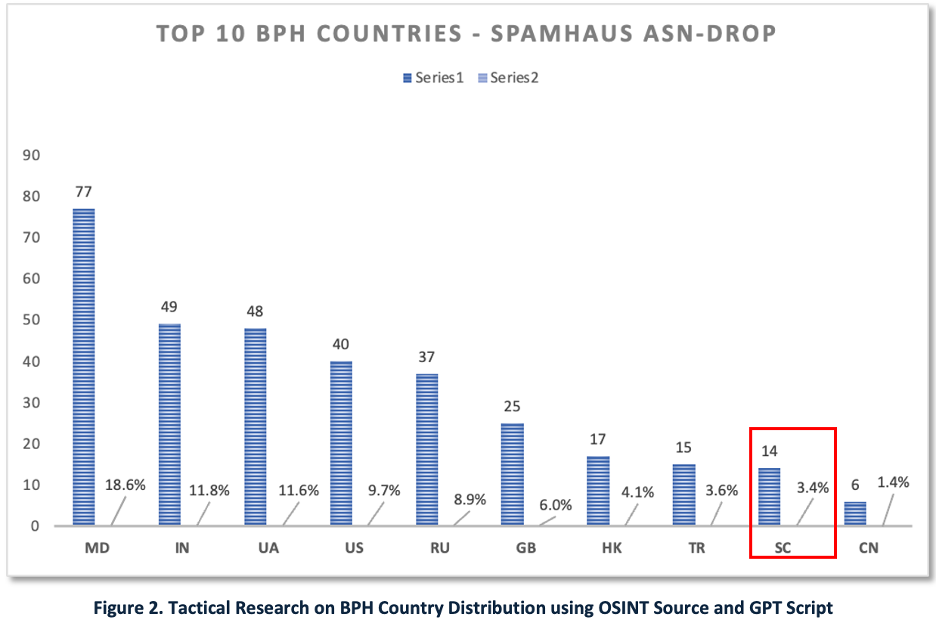
This lead tipped the analyst to pivot to OSINT, using the Spamhaus – ASN-Drop feed of 400+ ASNs tied to cybercrime/BPH. The analyst downloads the JSON, prompts GenAI to convert to CSV, and charts results in Excel (Figure 2). Seychelles (SC) appears among top BPH-linked ASNs; several top-10 countries align with “regulatory safe haven” patterns from Figure 1.
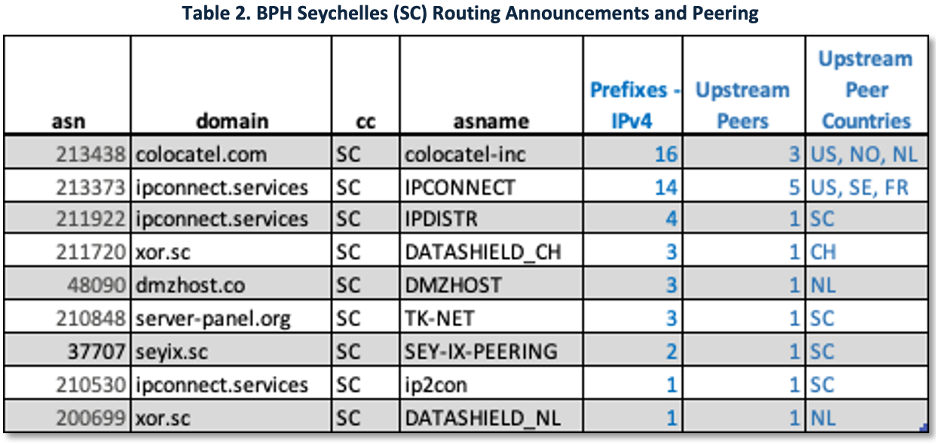
Next, the analyst wants to assess the resilience of the BPH based on its ASN peering relationships. With Cloudflare Radar, the analyst enriches Spamhaus rows to examine upstream relationships. Table 2 shows columns 1–4 from Spamhaus and 5–7 from Radar. Seven of nine Seychelles ASNs appear to be stub ASNs (single upstream), with upstream peers located in cooperative jurisdictions – a cue for takedown/escalation strategy.
Continuing with the scenario, the analyst asks GenAI to draft Python that automates ASN lookups and enrichment (Figure 3). If feasible, engineering can wrap this into an agent to streamline future cases.
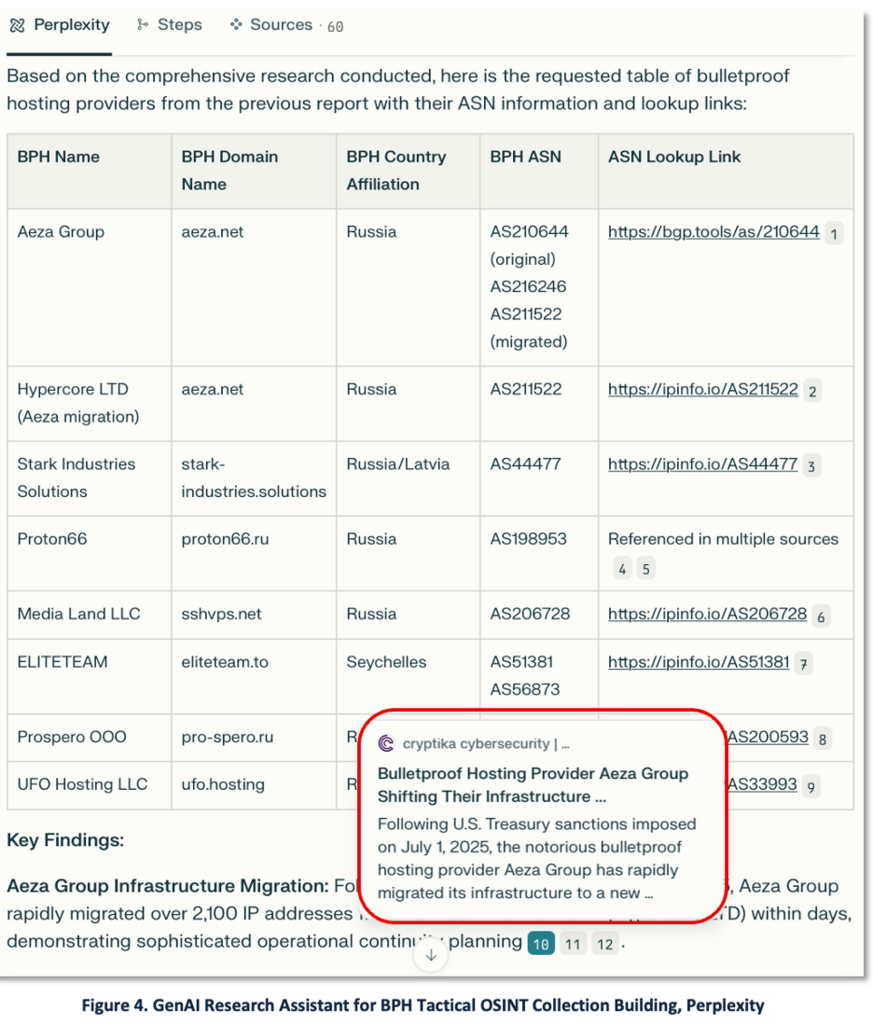
To complete the scenario, the analyst builds a working catalog. The analyst prompts GenAI to assemble a BPH collection (name, domain, country, ASN, lookup reference) – see Figure 4 (Perplexity output).
Enforcement Actions
CTI analysts support enforcement actions for BPH investigations. The scenarios below were vetted with trusted government counterparts involved in cybercrime and nation-state cases. Major application areas:
Law enforcement: Investigations can lead to domain seizures/suspensions, server seizures, sanctions, indictments, arrests, and prosecutions, often across borders. Recent examples include:
- Operation Endgame (2024 -2025): International operation that resulted in takedowns across the malware-dropper ecosystem, with hundreds of servers and thousands of domains seized, plus multiple arrests/warrants [27].
- U.S. Treasury sanctions: (July 2025] against BPH providers Azea Group and Zservers [18].
- August 2025: U.S. Indictments and domain seizures tied to a Chinese-based fentanyl trafficking network[23].
Phishing and Brand Protection Domain Takedowns: The Anti-Phishing Working Group, APWG, reported detections of more than 1 million phishing detections in Q1 2025. In 2024, ICANN (Internet Corporation for Assigned Names and Numbers) recorded 20,000+ registrar/registry complaints, leading to ~200 investigations and ~2,700 domain suspensions.
Domain Takedown Managed Services: Domain takedowns are a multi-party administrative process well suited to ML/GenAI assistance. Industry estimates place the 2025 domain takedowns-as-a-service market at ~ $500 million.
How GenAI can support enforcement:
- Case triage & clustering: Group abuse reports by ASN/host/registrar to surface BPH patterns and re-homing.
- Evidence packs: Generate registrar/registry takedown templates (WHOIS, DNS, hosting trail, screenshots), law-enforcement-ready affidavits, and STIX bundles; auto-translate for cross-border submissions.
- Attribution scaffolding: Map entities from IP → ASN → reseller → payment to identify enablers and jurisdictions.
- Playbook orchestration: Use RAG (Retrieval-Augmented Generation) to retrieve registrar/TLD requirements, track SLAs, and produce executive briefs and LE (Law Enforcement) referral memos and after action reports.
Bottom line: CTI adds measurable value when high-fidelity evidence is paired with repeatable playbooks – enabling faster suspensions, seizures, sanctions, and prosecutions against BPH-enabled operations.
Outlook
Rising awareness of cyber risk, the scale of Internet infrastructure, and the creativity and persistence of threat actors point to continued demand for skilled CTI analysts and RFI Desk services.
As Google and Recorded Future emphasize, defenders need a comprehensive approach: treat cybercrime as a national-security issue, strengthen baseline defenses, disrupt key enablers (including bulletproof hosting), and deepen international cooperation [8,9]. The ecosystem’s modular supply chain means single takedowns seldom last; sustained, coordinated pressure is essential.
Two technologies where stronger international oversight are urgently needed are the Domain Name System (DNS) and Internet routing. DNS and IP routing represent the basic mechanics of the global internet. And both suffer from weak governance and complicated economic models that undermine Internet security and safety. For example:
- Domain Name System (DNS). A global industry of roughly $4–5B is overseen by ICANN, a multi-stakeholder nonprofit funded largely by registries/registrars – creating incentives that can complicate abuse mitigation. More consistent enforcement, clearer SLAs for abuse handling, and better data sharing are needed.
- Internet routing. Routing policy is set by individual networks (ASNs) and informed by IETF standards. ICANN’s affiliate PTI operates the IANA (Internet Assigned Numbers Authority), which allocates top-level IPv4/IPv6 and ASN blocks to Regional Internet Registries (RIRs) under globally agreed policies. As IANA does not control BGP, economic incentives around IPv4 leasing and uneven RPKI (Resource Public Key Infrastructure) adoption continue to create openings that criminals exploit.
None of this is new, but the stakes are higher. The path forward is clear: combine fast, evidence-rich CTI with repeatable takedown playbooks; invest in identity, email/DNS authentication, and routing hygiene; and work collaboratively and internationally in legal, technical, and financial actions against BPH providers, enablers, and customers.
Editor’s Notes:
- We used GenAI assistants (ChatGPT-4o, ThreatShare.ai Cyber Researcher, Google Gemini, Claude, Perplexity) for search, brainstorming, summarization, enrichment, code generation, and editorial review.
- The featured image was generated from a prompt to ChatGPT.
References
- SANS – SANS 2025 CTI Survey Navigating Uncertainty in Today’s Threat Landscape, May 2025
- Cyber Security Tribe – US Cybersecurity Recruitment Trends for 2025, 2-April-2025
- Google Cloud Blog – Too many threats, too much data, say security and IT leaders. Here’s how to fix that, 28-July-2025
- Silent Push – Webinar – Mapping the Dark: Exposing the Depths of Bulletproof Hosting Providers, 14-July-2025.
- Intel471 – Zservers: Bulletproof hosting for online crime, 11-March-2025
- DomainTools – Domain Registrars Powering Russian Disinformation: A Deep Dive into Tactics and Trends , 18-March-2025
- KrebsonSecurity – Stark Industries Solutions: An Iron Hammer in the Cloud, 23-May-2024
- Google Cloud – Cybercrime: A Multifaceted National Security Threat, 11-Feb-2025
- Recorded Future: Insikt Group – 2024 Malicious Infrastructure Report, 28-Feb-2025
- The Washington Post – China’s cyber sector amplifies Beijing’s hacking of U.S. targets, 16-July-2025
- Trend Micro – Bridging Divides, Transcending Borders: The. Current State of the English Underground, 5-Jan-2025
- Spamhaus – ASN-Drop JSON: https://www.spamhaus.org/drop/asndrop.json
- BitSight – On the Move: Fast Flux in the Modern Threat Landscape, 15-July-2025
- Wired – Cybercriminals Are Hiding Malicious Web Traffic in Plain Sight, 6-June-2025
- SOCRadar – Operation Eastwood Targets NoName057(16) in Global Crackdown, 16-July-2025
- Cybercrime Information Center – Phishing Activity in Domain Registrars, November 1, 2024 – January 31, 2025
- Silent Push – Silent Push IOFA™ Feed Detects Aeza Group Infrastructure Shift Following OFAC Sanctions, 24-July-2025.
- U.S. Department of Treasury – Treasury Sanctions Global Bulletproof Hosting Service Enabling Cybercriminals and Technology Theft, 1-July-2025
- Information Security Management Group – US Sanctions Crypto Exchange Tied to Russian Ransomware, 14-Aug-2025
- ASD (Australian Signals Directorate) – “Bulletproof” hosting providers Cracks in the armour of cybercriminal infrastructure, 22-Jan-2025
- CISA Cybersecurity Advisory, Alert Code AA25-093A – Fast Flux: A National Security Threat, 3-April-2025
- Information Security Management Group – Rise of Chaos Ransomware Tied to BlackSuit Group’s Exit, 28-July-2025
- Bellingcat – A Chinese Fentanyl Smuggling Network’s Footprints in Japan, 7-Aug-2025
- Flashpoint – The Future of Threat Intelligence: Meeting the Moment with Purposeful AI, 5-Aug-2025
- DNS Research Federation – Are DNS Abuse Mitigation Efforts Keeping Up? New Data on ICANN’s 2024 RAA Amendments Suggests Gaps Remain , 9-April-2025
- ICANN – ICANN Domain Metrica Release Update: Access Now Open to All Users, 18-Feb-2025
- Europol – Operation ENDGAME strikes again: the ransomware kill chain broken at its source, 22-May-2025