Category: Domains
Domain related posts
From the Praetorian Guard of Rome to Swiss Guard mercenaries of nobility to the armies of white collar advisors and defenders of today, financial institutions and wealthy families expend vast resources protecting their wealth. In…
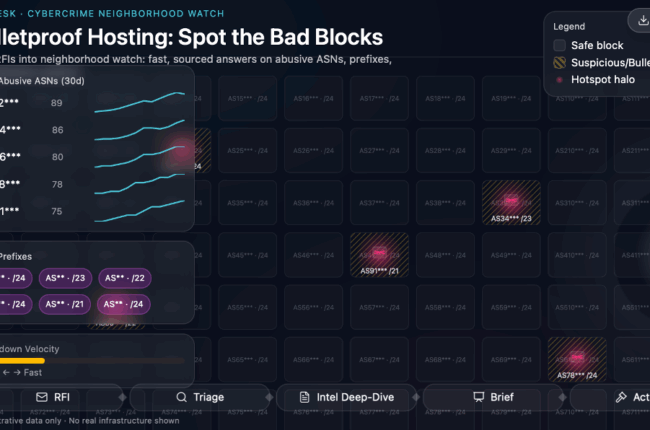
As GenAI and cyber incidents dominate headlines, cyber threat intelligence (CTI) teams in large enterprises are seeing a sustained surge of requests for information (RFIs) from executives, colleagues, customers, and partners. It is a surge…
Summer reading lists offer a change of pace and often include crime stories. So in this post, we’re switching from our more strategic and sector specific topics, to a cybercrime case. And right on cue,…
Recent reports from multiple trusted sources (CERT-UA, Microsoft Threat Intelligence, Lumen) published in December 2024, highlight ongoing Russian state-sponsored cyber espionage campaigns targeting Ukrainian drone operators and defense contractors. [1-4] The threat actors behind these…
On 22-October-2024, The Computer Emergency Report Team of Ukraine (CERT-UA) and Amazon issued Cyber Threat Intelligence (CTI) alerts. Microsoft followed with a detailed blog post on 29-October. These alerts described a targeted phishing and espionage…
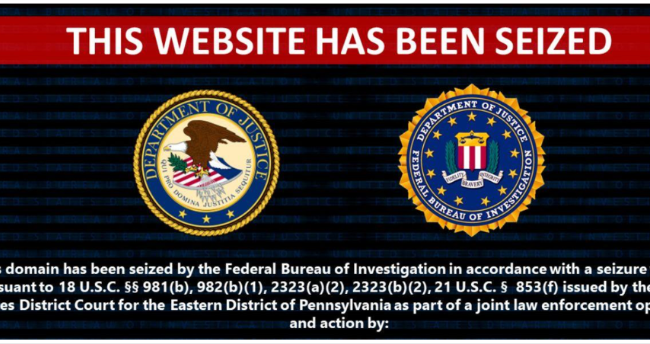
Big Events have a way of changing editorial calendars. Before taking a brief Labor Day break, Iran’s Election Interference was next on our calendar. But things changed on 4-September with DOJ’s court filings on Russian…
We are now twelve days (July 18-29) into the CrowdStrike Outage incident. While its impact and scale may be unprecedented, recovery operations are winding down. In this follow-on to our July 24th Flash Report, we provide:…
We are now in day 6 (July 18 – 23) of the Internet outage caused by a defective CrowdStrike software update. In this post, we focus on one aspect of the story – the tracking,…
Initially, this post was intended to be a routine review of how cyber threat actors utilize domain names and DNS infrastructure, how these uses evolve, and how cyber threat analysts can use DNS intelligence to…