Summer reading lists offer a change of pace and often include crime stories. So in this post, we’re switching from our more strategic and sector specific topics, to a cybercrime case. And right on cue, the U.S. Department of the Treasury’s announcement on May 29th of sanctions against Funnull Technology Inc. for its role in a wide-ranging, multi-year “pig butchering” fraud campaign sets the stage.
In this post, we will:
- Review details of the Funnull pig butchering campaign, based on FBI alerts and supporting industry research.
- Demonstrate how cyber threat analysts can use GenAI to augment their domain name intelligence (DNI) playbooks across fraud investigations, adversary tracking, brand protection, and threat hunting.
- Offer an outlook on the impact of fake AI in cybercrime, the need for proactive DNI solutions, and new industry efforts to standardize threat actor taxonomy.
Summary: Domain name intelligence (DNI) plays an essential role in cybersecurity, yet it remains a niche capability on many security teams. While GenAI offers promising tools that can enhance DNI workflows, adoption remains limited. Given the scarcity of skilled DNI analysts, integrating GenAI into the DNI playbook can deliver more effective and scalable threat intelligence operations.
Funnull Case-Study
The case against Funnull Technology Inc. (Funnull) and Liu Lizhi (Liu), a Chinese national and administrator of Funnull, is detailed in the May 29th filings by the FBI, the U.S. Department of the Treasury, and the Office of Foreign Assets and Control – OFAC [1-3].
These findings were informed in large part by open-source intelligence (OSINT) from cybersecurity researchers and journalists who uncovered and shared technical indicators and evidence. Key contributors include:: Sansec 6-25-2024 [4], Cloudflare 6-26-2024 [5], Silent Push 10-22-2024 [7-8], KrebsOnSecurity 1-30-2025 [9-10], and Chainalysis 5-29-2025 [11]. Additional insights came from respected media sources such as The Register [6], South China Morning Post (SCMP) [12], and The Record from Recorded Future News [13].
A composite summary of these findings follows:
Economic Scale: Funnull accounts for the majority of cryptocurrency investment scam websites reported to the FBI. Conservative estimates suggest U.S. victims lost approximately $200 million, with average losses exceeding $150,000 per individual [2].
Scope: The FBI Alert covers activity from October 2023 to April 2025, focusing on domain name and network infrastructure linked to cryptocurrency investment fraud scams.
Actor: OFAC lists Funnull’s company location as the Philippines and identifies Liu Lizhi’s location as China. Other claims about Funnull’s origins are murky. The Register reports conflicting claims including Slovenia, the UK, and even the U.S., none of which could be confirmed. Funnull emerged around 2022 as a criminal content delivery network (CDN) provider. It is linked to other criminal entities such as Fangneng CDN and appears to be owned by ACB Group. It is also associated with Suncity Group, a transnational Chinese crime syndicate involved in laundering billions of dollars for Chinese criminal groups and North Korea’s Lazarus Group [6–9]. Chainalysis reported Funnull “had direct exposure to Huione Pay, for which the U.S. Department of the Treasury’s Financial Crimes Enforcement Network (FinCEN) recently issued a finding and notice of proposed rulemaking (NPRM) identifying it as a primary money laundering concern. Additionally, the addresses show indirect exposure to various types of scams and domain management infrastructure vendors [11].”
Campaigns: Funnull’s CDN infrastructure has been used in numerous cybercrime campaigns, including fake trading apps, pig butchering scams, gambling websites, retail phishing, and the polyfill[.]io supply chain attack. In that attack, over 100,000 legitimate users of a popular open-source code library were redirected to malicious sites [4, 5, 7, 10].
Supporting Domain Infrastructure: Since January 2025, the FBI has identified 548 unique Funnull canonical names (CNAMEs) linked to over 332,000 unique domains [3]. Silent Push research found over 200,000 unique hostnames proxied through Funnull, with most using domains generated via domain generation algorithms (DGAs). Both Silent Push and KrebsOnSecurity describe this operation as “infrastructure laundering”—a tactic similar to bulletproof hosting, in which cybercriminal services lease IP space from legitimate cloud providers and relay malicious traffic through trusted U.S.-based platforms such as Amazon and Microsoft [7, 10].
Mitigations: The FBI places responsibility in part on infrastructure providers, specifically domain name system (DNS) and internet service providers (ISPs). In operations involving infrastructure laundering and bulletproof hosting, responsibility for action falls heavily on those providers. Under U.S. sanctions law, entities and assets designated as sanctioned must be blocked. However, outside of sanctions, it is often difficult for enterprises to compel hosting or cloud providers to take down malicious infrastructure. Enterprises must proactively monitor and hunt for domain-based threats.
Analyst Use-cases
In this section, we highlight practical use cases from our Funnull investigation. These examples show how Cyber Threat Intelligence (CTI) and Domain Name Intelligence (DNI) analysts can use GenAI and DNI platforms to support threat intelligence operations.
Usecase 1: Ad hoc Research
A significant part of the CTI and DNI analyst’s role involves monitoring open sources for actionable intelligence. Given the sheer volume of threat reports from both the open and dark web, exacerbated by AI-generated slop, keeping pace is a constant challenge.
Traditionally, analysts have relied on RSS feeds, CTI subscriptions, open-source threat intelligence, threat portals, and search engines to build and manage collections. While these tools remain essential, GenAI—when tuned to an organization’s needs—offers analysts a powerful capability for handling ad hoc research and RFIs (Requests for Information).
For each use case in this scenario, we include screenshots generated through iterative prompt dialogs with our custom implementation, ThreatShare.ai Cyber Researcher, built on OpenAI’s ChatGPT-4o. This version is customized for cybersecurity workflows and data, and includes a source-link verification feature to mitigate hallucinations and highlight authoritative citations.
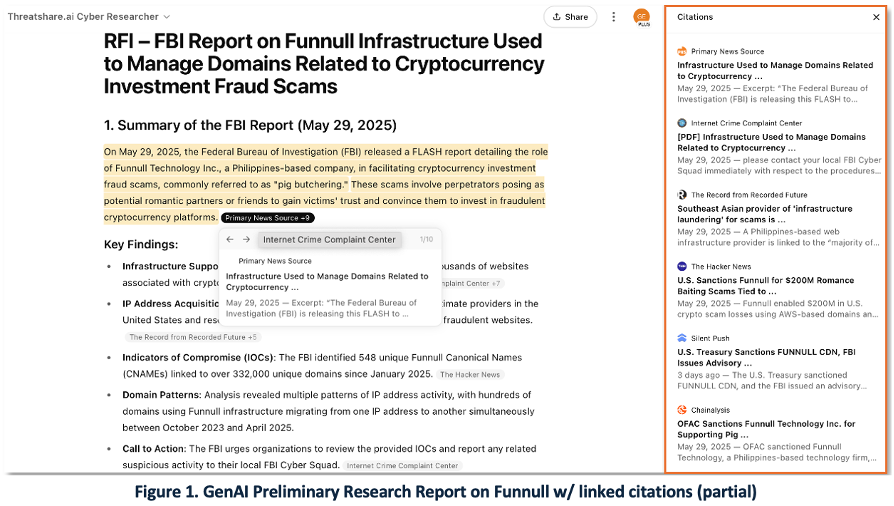
Figure 1 shows a partial view of a 3-page Funnull report generated in response to an RFI. Note the FBI report summary and citation pop-up in the center, with additional linked sources displayed in the right-hand citation panel.
Usecase 2: Python Generation
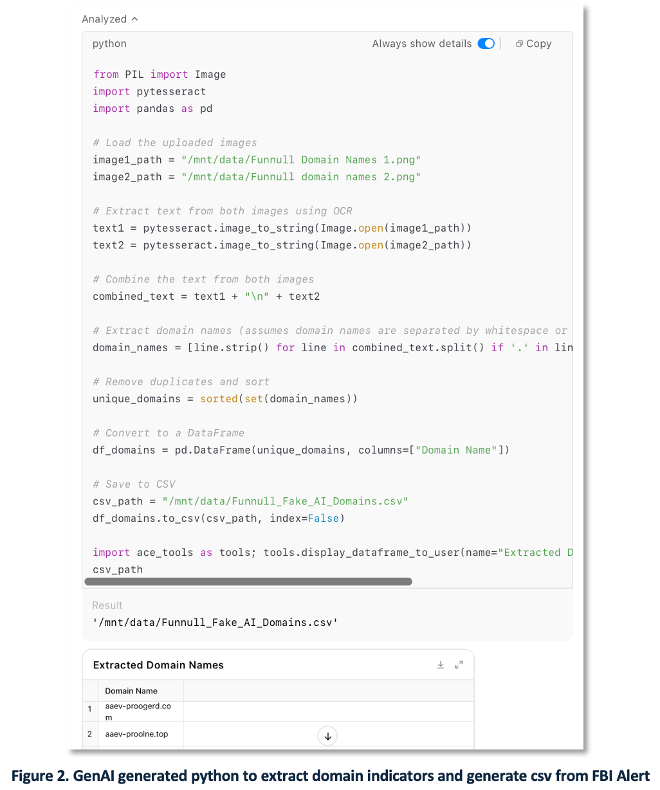
Another common analyst task is extracting indicators from unstructured formats such as PDFs or HTML pages. While some sources offer downloadable IOCs in CSV or JSON formats, many do not. In our case, we asked the GenAI to generate a Python script that could extract domain indicators from the FBI Funnull alert and export them to CSV.
Figure 2 displays the script used to extract domains and generate a structured CSV output.
Usecase 3: Domain lexical and semantic analysis
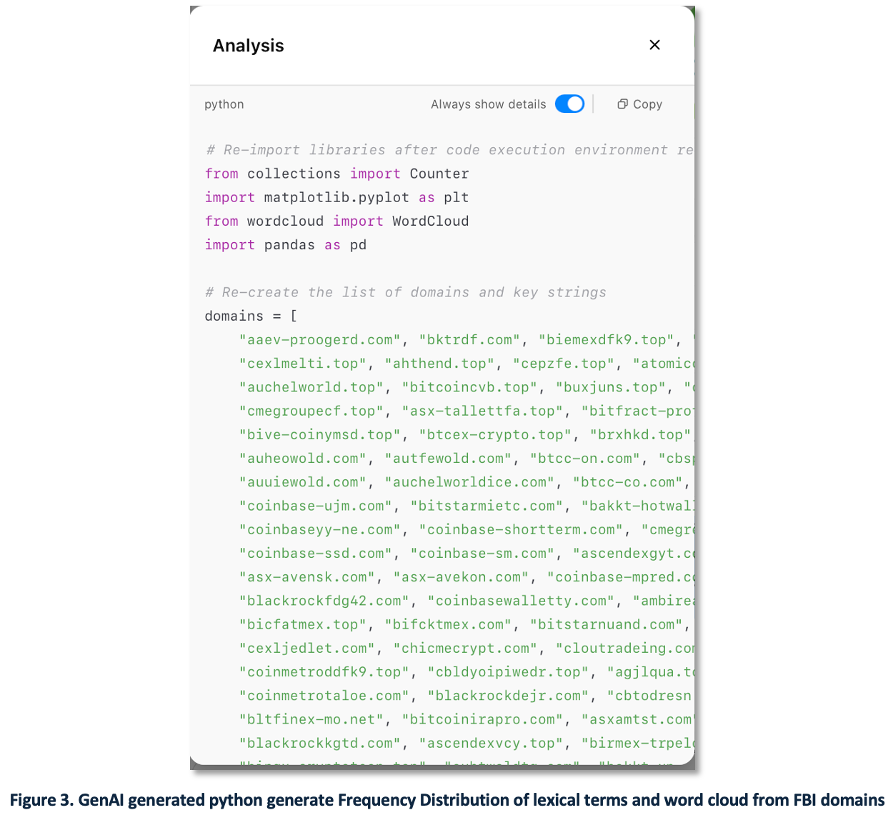
Continuing the Funnull use case, we next asked the GenAI to perform lexical analysis of domain names. Our goal was to identify recurring text strings (tokens) used by adversaries in domain registrations.
We prompted the GPT to generate a frequency distribution of domain terms and visualize the results with a word cloud. Figure 3 shows the Python code used for this task.
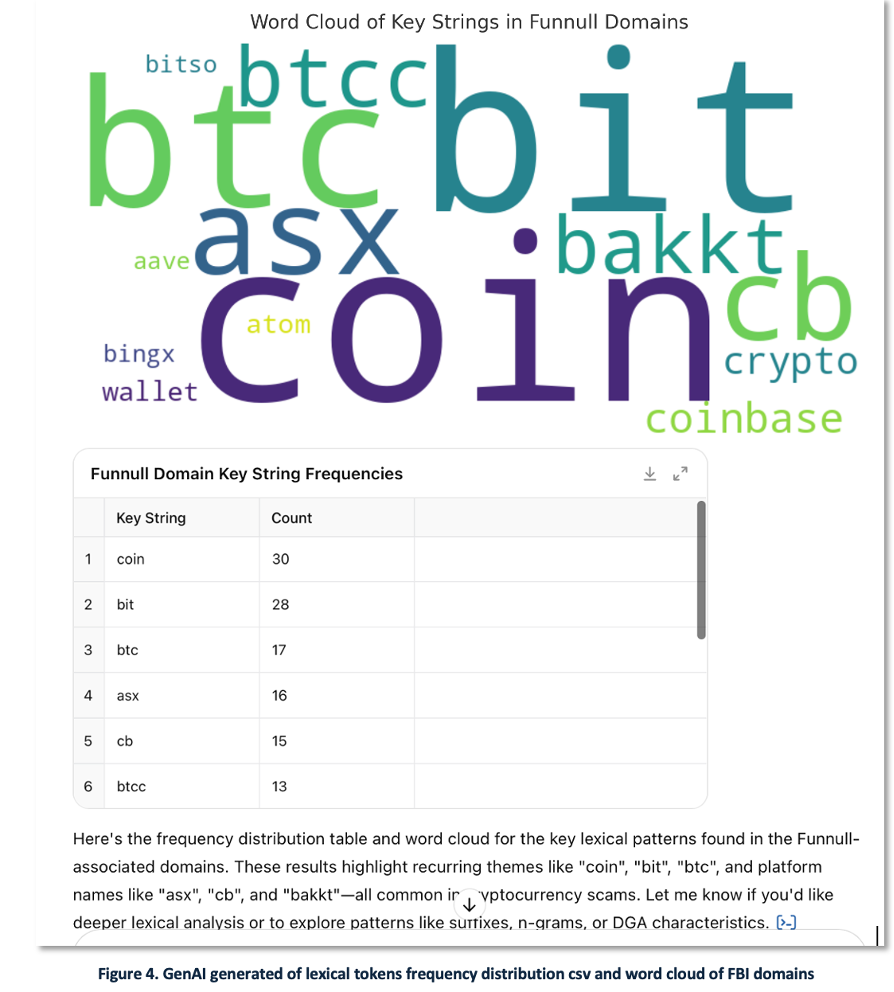
In Figure 4, we see a sample of the frequency table and word cloud, which reveal the semantic patterns in domain usage. Terms such as “coin”, “btc”, and “bit” appear prominently, as expected given the cryptocurrency focus of the campaign. This kind of analysis helps analysts understand adversary TTPs and can be used to proactively monitor for newly registered domains containing high-risk tokens.
Usecase 4: DNS infrastructure statistical analysis
After generating a CSV of extracted domains, the next step in the analyst’s workflow might be to enrich those domains using a DNI platform like Silent Push or DomainTools.
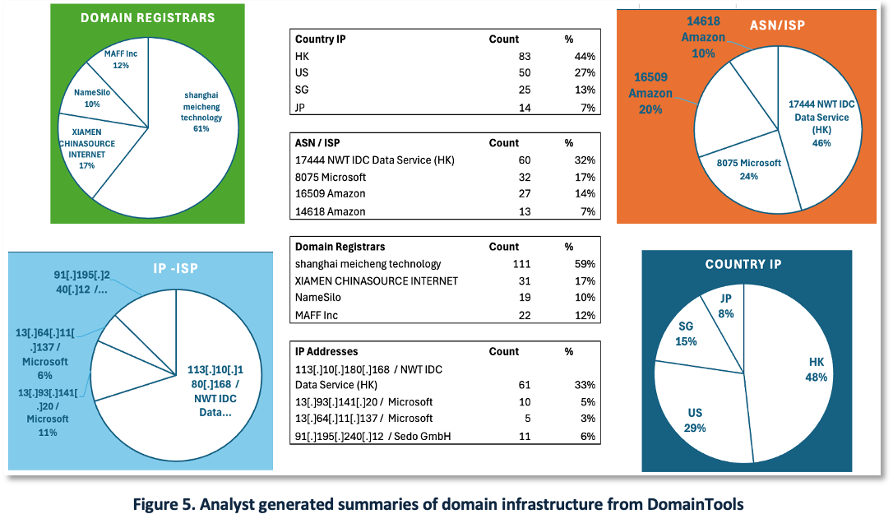
In Figure 5, we show a summary report created in Excel using data from DomainTools. The analyst aggregated metadata on registrars, IP addresses, ASNs, and geolocation to build an infrastructure profile. This type of report can inform threat hunting, enrichment, and attribution efforts.
Outlook
Adversarial AI Makes Phishing Easier
Adversarial AI is making it easier for threat actors to plan, craft, and launch sophisticated phishing campaigns. As these tools improve, phishing attacks are becoming more frequent and convincing. In just the past month, reports from Mandiant, Morphisec, and Check Point Research have detailed new campaigns using fake AI video-generation websites to lure victims into credential theft or malware downloads [14–16]. Mandiant attributes one such campaign to a Vietnamese threat actor tracked as UNC6032.
Deep Fakes Makes Pig Butchering Attacks More Potent
A recent Wired podcast on the most serious cyber-attacks facing America, highlighted how deepfake technology is being used to amplify pig butchering scams. These schemes now include deepfake video and voice content to impersonate romantic partners or financial advisors. Wired noted listings on dark web marketplaces offering deepfake kits specifically designed to impersonate a victim’s face and voice—tools that make these scams even harder to detect.
A Unified Cybersecurity Adversary Taxonomy
A persistent challenge in the cybersecurity industry has been the inconsistent naming of threat actors. Leading firms such as CrowdStrike, Mandiant, Microsoft, and Palo Alto Networks have historically used different names for the same adversary groups, creating confusion and inefficiencies across security teams and reporting.
In a long-overdue development, these companies have now committed to working toward a standardized adversary taxonomy [19–21]. This initiative will help streamline communication, improve attribution, and enhance collaboration across the industry.
Editor’s Notes:
- Thanks to our GenAI assistants for research assistance and editorial review: ChatGPT-4o, ThreatShare.ai Cyber Researcher, Google Gemini AI, and Perplexity.
References
- IC3.gov Flash # 20250529-001 – Infrastructure Used to Manage Domains Related to Cryptocurrency Investment Fraud Scams between October 2023 and April 2025, 29-May-2025
- U.S. Department of the Treasury – Treasury Takes Action Against Major Cyber Scam Facilitator, 29-May-2025
- Office of Foreign Assets Control – https://ofac.treasury.gov/recent-actions/20250529, 29-May-2025 Office of Foreign Assets Control
- Sansec.io – Polyfill supply chain attack hits 100K+ sites, 25-June-2025
- Cloudflare – Automatically replacing polyfill.io links with Cloudflare’s mirror for a safer Internet, 26-June-2024
- The Register – Polyfill.io owner punches back at ‘malicious defamation’ amid domain shutdown, 28-June-2024
- Silent Push – Unveiling Triad Nexus: How FUNNULL CDN Facilitates Widespread Cyber Threats., 22-Oct-2024
- Silent Push – Infrastructure Laundering: Silent Push Exposes Cloudy Behavior Around FUNNULL CDN Renting IPs from Big Tech, 30-Jan-2025
- KrebsOnSecurity – U.S. Sanctions Cloud Provider ‘Funnull’ as Top Source of ‘Pig Butchering’ Scams, 29-May-2025
- KrebsOnSecurity – Infrastructure Laundering: Blending in with the Cloud, 30-Jan-2025
- Chainalysis – OFAC Sanctions Funnull Technology Inc. for Supporting Pig Butchering Scams, 29-May-2025
- SCMP (South China Morning Post) – US sanctions Philippine tech firm over ‘pig butchering’ scams that took US$200 million, 3-June-2025
- Recorded Future | The Record – Southeast Asian provider of ‘infrastructure laundering’ for scams is sanctioned by US? , 29-May-2025
- Mandiant: Text-to-Malware: How Cybercriminals Weaponize Fake AI-Themed Websites, 27-May-2025
- Morphisec – New Noodlophile Stealer Distributes Via Fake AI Video Generation Platforms, 8-May-2025
- Check Point Research – THE STING OF FAKE KLING: FACEBOOK MALVERTISING LURES VICTIMS TO FAKE AI GENERATION WEBSITE, 20-May-2025
- SC Media – Mandiant finds more than 30 fake AI websites spreading malware, 27-May-2025
- Wired – Every Cyber Attack Facing America, 2-June-2025
- Reuters – ‘Forest Blizzard’ vs ‘Fancy Bear’ – cyber companies hope to untangle weird hacker nicknames, 2-June-2025
- CrowdStrike – CrowdStrike and Microsoft Unite to Harmonize Cyber Threat Attribution, 2-June-2025
- Microsoft – Announcing a new strategic collaboration to bring clarity to threat actor naming, 2-June-2025